Cybersecurity is the number one risk facing enterprises today, and yet organizations remain dangerously unprepared. Executives are not blind to the problem — they understand the financial exposure, the reputational stakes, and the business impact of a major breach. They acknowledge gaps in their defenses and recognize the vulnerabilities that could cripple their mission-critical systems. But awareness has not translated into readiness and true business resilience remains elusive for the vast majority of firms. Data strategies are especially important – specifically data governance, data protection, and data quality. These remain essential elements of cyber resilience, but they’re only part of the equation. True business resilience requires confronting a multitude of dimensions — from application security to identity, supply chain integrity, operational continuity, infrastructure defenses and more. The uncomfortable truth is that most firms still lack the cohesive strategy, investment, and execution to protect their most vital assets.
In this Breaking Analysis, we share data from a recent survey done by theCUBE Research that quantifies this reality. We’ll unpack what it means for technology buyers who must navigate escalating risks, for vendors seeking to align their solutions to market demand, and for industries where data is not just a byproduct but the lifeblood of competitive advantage. We’ll also share some ETR spending data on pure play data protection tech companies, which are each pivoting their messaging and portfolios toward cyber resilience.
What Keeps Jamie Dimon up at Night?
But before we get into the survey data we wanted to share a brief clip from the Acquired Podcast. Recently they hosted Jamie Dimon and asked him what worries him what are the risks that keep him up at night. And Dimon mentioned some risk factors in banking like asset prices but here’s what he said was the most pressing concern:
And then, the other thing, the biggest risk to me is cyber. I mean, I think the cyber stuff, we’re very good at it. We work with all the government agencies. They would say that [we’re very good]; we spend $ 800 million a year or something [like that] on it. We educate people on it, we just do [everything we can]… But you’re talking about grids and communications companies [and critical infrastructure]… -Jamie Dimon
Setting the Stage: Why this Research Matters
Our latest survey underscores a sobering reality: cyber remains the number one business risk, yet most organizations are not fully prepared to address it. The goal of this research was to go beyond anecdote and provide a data-driven assessment of where organizations stand, what challenges they face, and what best practices look like in practice.
The study was fielded in Q1 2025 with 600 qualified respondents across North America, Western Europe, and Asia Pacific. Three quarters of the respondents came from large enterprises with more than 1,000 employees, while the remaining quarter represented midmarket firms. Importantly, the survey deliberately balanced perspectives from both IT and cybersecurity professionals, giving us a rare A/B comparison between operational and security-centric worldviews.
We believe this distinction is critical. Security is no longer a bolt-on function; security teams are increasingly influencing infrastructure and application decisions across the enterprise. This survey allowed us to examine how that shift manifests in real-world practices.
Survey Objectives and Framework
The research was structured around the NIST Cybersecurity Framework, which remains the most widely adopted common language for resilience across industries. The objectives were fourfold:
- Gain insight into proactive and reactive strategies organizations use to ensure robust cyber resilience.
- Examine the state of resilience against the NIST2 framework across multiple dimensions.
- Identify specific technology and process trends spanning data management, networking, backup, and recovery.
- Determine the overall state of the market and where best practices are emerging.

Why This Matters
Our research indicates that the market is at an inflection point. Organizations are keenly aware of their gaps, but translating awareness into readiness is still challenging. The juxtaposition of IT and cybersecurity respondents highlights a growing convergence of responsibilities, with security teams asserting more influence over decision-making than ever before.
In our view, this blending of perspectives will redefine how enterprises invest in infrastructure and resilience strategies over the next several years. The data from this survey provides an empirical foundation for understanding that shift.
The Costly Reality of Cyber Disruptions
The data paints a stark picture, i.e. cyber incidents are not isolated anomalies — they are a recurring and costly reality for most organizations. Nearly two-thirds of respondents reported experiencing at least one cyberattack in the past 12 months that led to financial or operational harm. Alarmingly, nearly a third of enterprises were hit more than once in that same period.
This frequency underscores a central point, specifically, cybersecurity risk is no longer a discrete IT problem; it is a systemic business risk with direct impact on both top-line revenue and bottom-line profitability. The scope of disruption extends far beyond stolen data into operational paralysis, regulatory exposure, reputational damage, and financial loss.
Key Findings from the Data
The survey asked organizations to identify all the consequences of their most recent impactful attack. The responses reveal a multi-dimensional crisis:
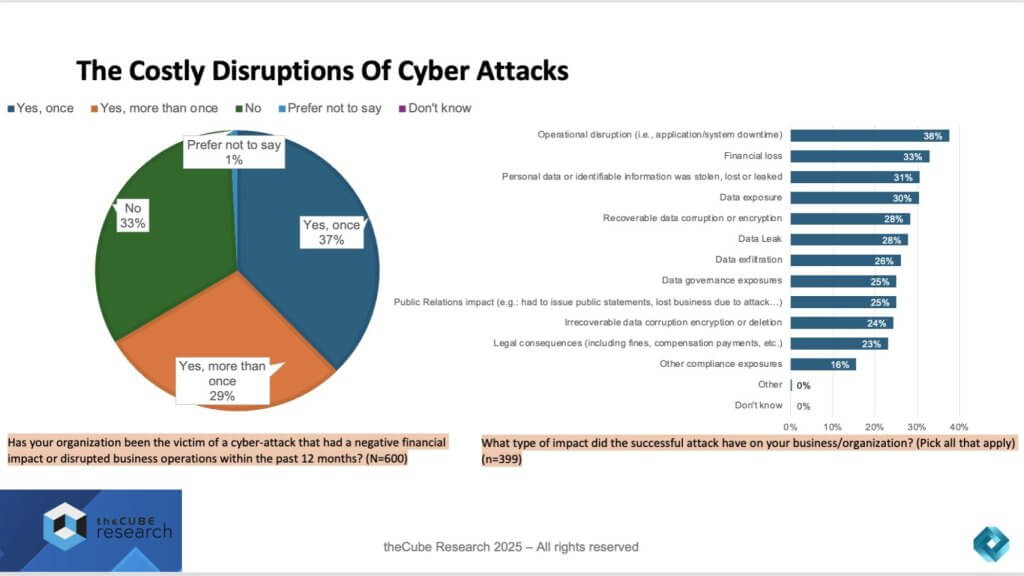
- Operational disruption (38%) topped the list, with downtime and system outages emerging as the most common — and most costly — business impact.
- Financial loss (33%) was the next most cited outcome, reinforcing the direct revenue and margin implications of attacks.
- Data compromise was pervasive, including personal data loss (31%), data exposure (30%), and both recoverable (28%) and irrecoverable (24%) corruption or encryption.
- Governance and compliance failures were widespread, with data governance exposures (25%), public relations fallout (25%), legal consequences (23%), and other compliance failures (16%) all prominently cited.
Taken together, the message is that organizations are not just facing a threat to confidentiality, but to the integrity and availability of their most critical resource — i.e. data.
Convergence in the Market
Our research indicates a convergence in the infrastructure market around three historically distinct domains:
- Backup and recovery technologies that were once viewed as insurance are now central to cyber resilience.
- Cybersecurity solutions are expanding beyond perimeter defense to encompass data protection and recovery.
- Data governance and compliance are emerging as equally critical, with regulatory risk amplifying the impact of breaches.
In our view, this convergence is reshaping the playbook for resilience. The bloodline of modern organizations is data and digital assets, not just physical assets. Attacks compromise the availability, trust, and utility of that data, directly undermining business continuity.
Looking forward, we believe this challenge is only going to be amplified by the rise of AI, which both demands high-quality data and introduces new vectors of risk. The ability to secure, govern, and recover data will become a core determinant of enterprise competitiveness in the digital economy.
Targeting the Weakest Link – No Part of the Infrastructure Is Safe
The data confirms what many practitioners already suspect – i.e. no layer of the digital infrastructure is immune from attack. Adversaries are systematic. They weigh the numerator — the potential benefit of an intrusion — against the denominator — i.e. the cost and difficulty of execution. Their mission is simple: maximize gain while minimizing effort. Defenders, therefore, must continually raise the denominator by hardening every layer. Yet the survey shows that attackers are finding weaknesses everywhere, from the systems meant to protect data, to the very AI workloads now powering digital transformation.
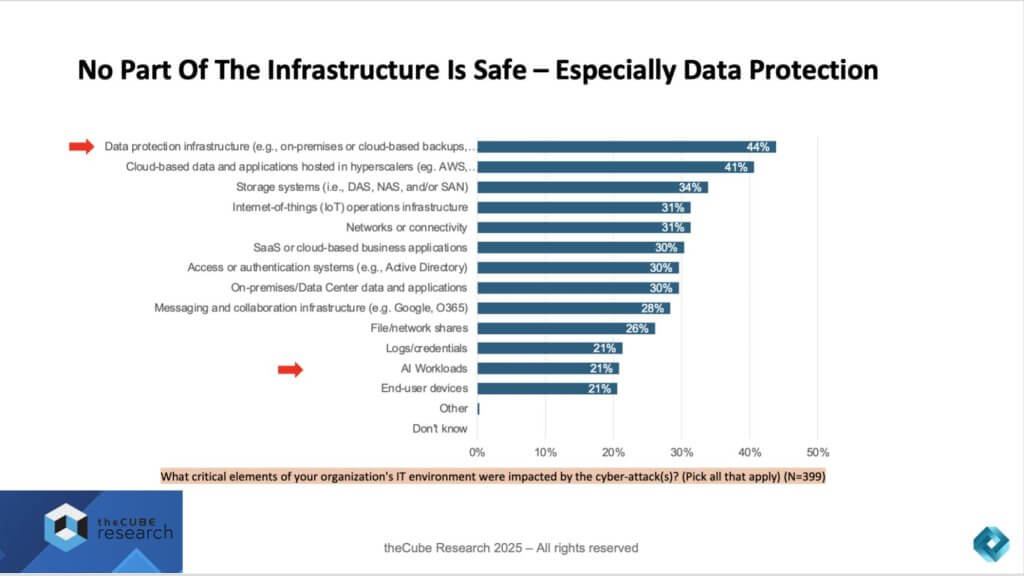
The most alarming insight is that data protection infrastructure itself is the number one target. At 44%, on-premises or cloud-based backups were the most frequently compromised component. This is a critical point that we can’t overemphasize. Once the backups are gone, recovery becomes nearly impossible, leaving organizations with little choice but to pay ransoms (which most often results in lost data despite the payment) or absorb devastating losses.
Breakdown of Vulnerable Targets
- Data protection infrastructure (44%) – Ironically, the “last line of defense” has become the first target. Attackers know that eliminating recovery options dramatically increases ransom leverage.
- Cloud-based applications and data (41%) – The hyperscaler environments that underpin modern IT remain prime targets, highlighting the complexity of securing multicloud deployments.
- Storage systems (34%) – DAS, NAS, and SAN environments continue to be compromised, with attackers exploiting gaps in patching, segmentation, and access control.
- IoT and networks (31%) – As more devices and edge assets are connected, adversaries exploit their weaker controls to gain entry.
- SaaS and authentication systems (30%) – Business-critical SaaS apps and Active Directory are frequent points of exposure.
- Emerging risks: AI workloads (21%) – Though lower on the list today, the rise of AI-powered applications creates new attack surfaces that are already being exploited.
Implications for the Enterprise
Our research indicates that cyber resiliency is not about protecting one component in isolation. It is about securing an interdependent system where weaknesses in one layer can compromise the whole. Two themes stand out:
- Holistic visibility and coverage – Enterprises must ensure they understand and monitor every component of the stack, from storage to SaaS to AI models. Attackers will probe until they find the least-defended link.
- Ecosystem interoperability – The lack of integration across tools and layers is itself a vulnerability. We believe the next wave of industry innovation will focus on stitching together ecosystems, driven by open APIs and, increasingly, consolidation through M&A.
In our view, the winners in this market will be the vendors that can provide comprehensive coverage across infrastructure layers while enabling interoperability. No single company can do it all, but the ones that integrate the most effectively will emerge as enterprise standards.
Many Incidents Are Ignored
This reality highlights a systemic issue: enterprises are drowning in alert fatigue. The sheer volume of events, compounded by false positives and the rising tide of AI-driven high-velocity attacks, makes it impractical for SecOps and IT teams to chase down every signal. The result is a massive exposure hiding in plain sight—threats that are not acted upon because organizations simply don’t have the capacity to investigate them all.
Implications for Security Operations
Our research indicates that ignoring alerts is a double-edged sword:
- Unknown risk exposure – By dismissing incidents without review, organizations effectively roll the dice on which alerts might represent genuine threats.
- Forensics gap – Many companies do not perform sufficient forensic analysis after incidents, which limits their ability to learn from past breaches and strengthen defenses.
- Volume vs. capability imbalance – The growth of machine-speed attacks is outpacing the human capacity to detect, classify, and respond.
The Role of AI in Closing the Gap
We believe this is where AI becomes a necessary ally. Automation can help organizations sift through massive volumes of alerts, applying real-time classification, prioritization, and pattern recognition that humans simply can’t achieve at scale. Several vendors and services providers are already delivering solutions that use AI to distinguish noise from signal and streamline response workflows.
In our view, the organizations that embrace AI-driven incident response will gain a decisive advantage. They will be better positioned to reduce ignored incidents, cut mean-time-to-detection, and harden their posture against advanced threats. Conversely, those who continue to let alerts pile up unaddressed are inviting avoidable risk into their environments.
The data shows the state of the market is not good—but the tools and partners exist to change that trajectory. The challenge is not whether solutions exist; it is whether organizations will prioritize and operationalize them fast enough.
Many Incidents Are Ignored
One of the more troubling findings from the survey is just how many security incidents are left unaddressed. Nearly half of the organizations admitted they ignore between 26% and 50% of all security alerts, even though they acknowledge these incidents could be valuable to investigate. Another 20% concede that they dismiss more than half of their alerts. Only a small minority — roughly 12% — report ignoring less than 10% of alerts.
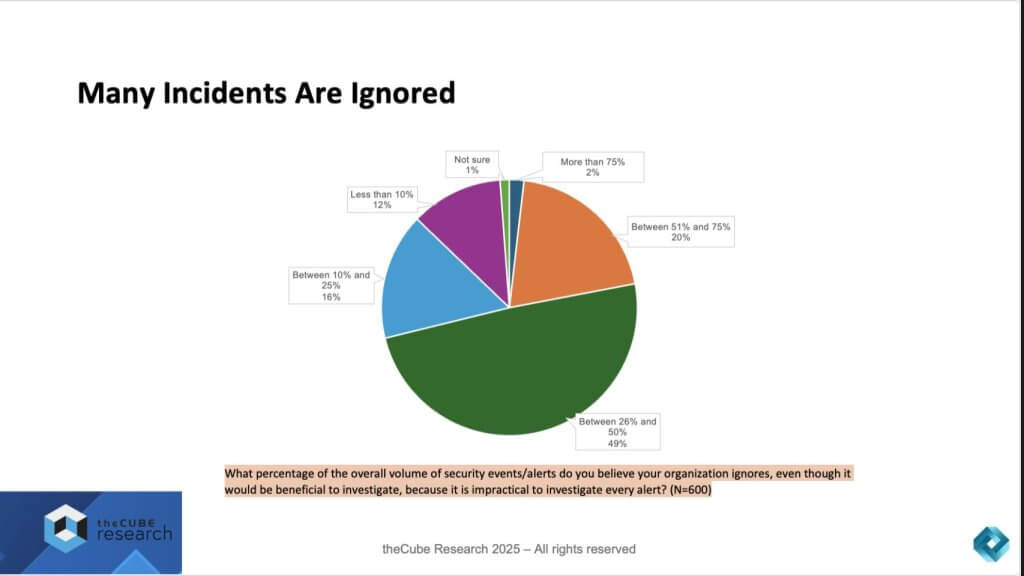
This reality highlights a systemic issue; enterprises are drowning in alert fatigue. The sheer volume of events, compounded by false positives and the rising tide of AI-driven high-velocity attacks, makes it impractical for SecOps and IT teams to chase down every signal. The result is a massive exposure hiding in plain sight — threats that are not acted upon because organizations simply don’t have the capacity to investigate them all.
Implications for Security Operations
Our research indicates that ignoring alerts is a double-edged sword:
- Unknown risk exposure – By dismissing incidents without review, organizations effectively roll the dice on which alerts might represent genuine threats.
- Forensics gap – Many companies do not perform sufficient forensic analysis after incidents, which limits their ability to learn from past breaches and strengthen defenses.
- Volume vs. capability imbalance – The growth of machine-speed attacks is outpacing the human capacity to detect, classify, and respond.
The Role of AI in Closing the Gap
We believe this is where AI becomes a necessary ally. Automation can help organizations sift through massive volumes of alerts, applying real-time classification, prioritization, and pattern recognition that humans simply can’t achieve at scale. Several vendors and services providers are already delivering solutions that use AI to distinguish noise from signal and streamline response workflows.
In our view, the organizations that embrace AI-driven incident response will gain a decisive advantage. They will be better positioned to reduce ignored incidents, cut mean-time-to-detection, and harden their posture against advanced threats. Conversely, those who continue to let alerts pile up unaddressed are inviting avoidable risk into their environments.
The data shows the state of the market is not good — but the tools and partners exist to change that trajectory. The challenge is not whether solutions exist; it is whether organizations will prioritize and operationalize them fast enough.
Even Mission-Critical Applications Are Highly Exposed
Perhaps the most sobering data point in the entire study is the lack of confidence organizations have in protecting their mission-critical applications. When asked what percentage of these applications are safeguarded by solutions that can guarantee an uncompromised, restorable copy of data, fewer than half of respondents could say with certainty that even 50% of their mission-critical workloads were fully protected.
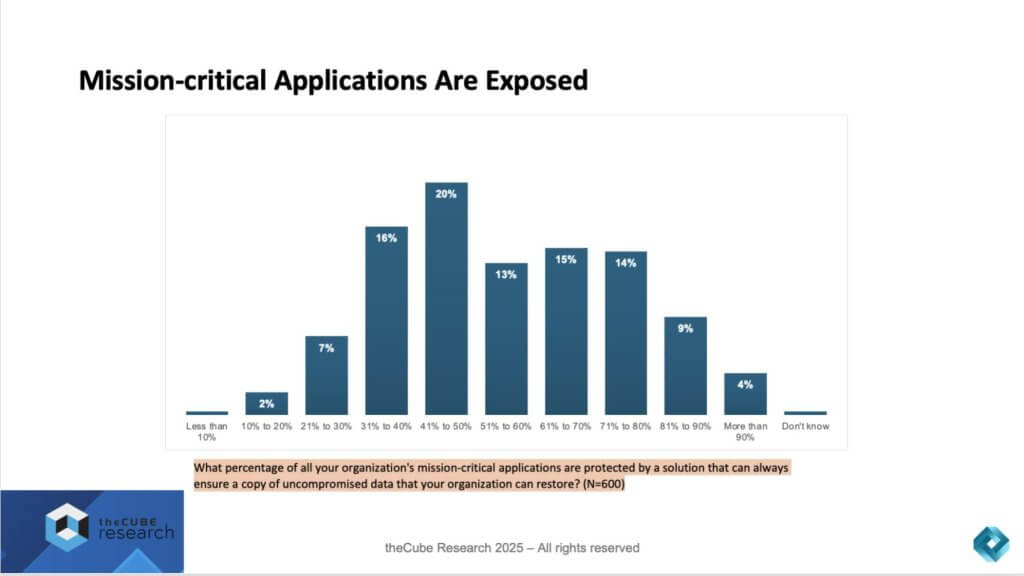
The distribution is striking:
- 36% reported that only between 31% and 50% of their mission-critical apps are reliably recoverable.
- Just 4% of organizations believe more than 90% of their critical apps are fully protected.
- A staggering proportion — well over half — operate in a gray zone where the ability to recover essential systems and data is uncertain.
This tells us that if the worst happens, many businesses may not be able to get back on their feet quickly, if at all.
Why This Matters
In our view, the inability to guarantee recoverability of mission-critical applications is a systemic failure. It is not simply an IT concern but a board-level issue with both operational and regulatory consequences. The risks are multi-dimensional:
- Business continuity – Outages directly impact revenue, productivity, and customer trust.
- Regulatory compliance – Losing regulated data or failing to prove chain of custody invites fines and reputational damage.
- Interdependence of systems – Mission-critical applications rarely exist in isolation; they span databases, structured and semi-structured data, SaaS systems, and hybrid cloud environments. A failure in one area cascades quickly across the ecosystem.
Raising the Bar
Our research indicates the only acceptable target is to get as close as possible to 100% recoverability. Anything less introduces unacceptable levels of business risk. While achieving this is undeniably difficult, the tools exist today to close the gap. The real challenge lies in aligning people, processes, and technology to enforce consistent, enterprise-wide resiliency.
We believe organizations that treat recoverability as a non-negotiable standard will be far better positioned to weather attacks, regulatory audits, and operational disruptions. Those that do not will increasingly find themselves vulnerable—not just to cybercriminals, but to competitors who can demonstrate greater resilience to customers, regulators, and shareholders alike.
Bye Bye Data: The Sobering Reality of Loss vs. Recovery
One of the most jarring findings in this research is the gap between data loss and data recovery outcomes following cyberattacks. The assumption many executives make — that backup and recovery investments will ensure near-complete restoration — simply does not align with reality on the ground.
On the left side of the chart, we see how much data organizations report being impacted during an attack. The most common outcomes are severe:
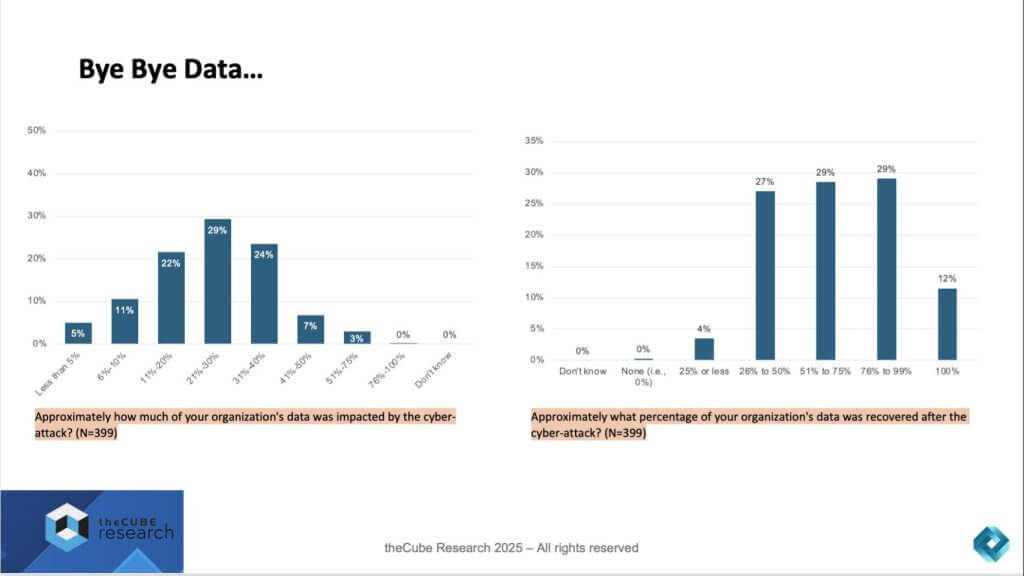
- 29% said between 21–30% of their data was affected.
- 24% experienced losses between 31–40%.
- Another 22% reported 11–20% of their data compromised.
In other words, for a significant portion of the market, between one-fifth and nearly half of all data can be put at risk in a single attack.
On the right side of the chart, recovery rates tell a story of partial wins and persistent gaps:
- The majority of firms (85%) were able to restore at least half of their data.
- 29% recovered between 51–75%, another 29% recovered 76–99%.
- Only 12% of organizations achieved a full 100% recovery.
Why the Gap Exists
Our research indicates this recovery shortfall is not due to a single factor, but rather a convergence of issues:
- Insufficient protection capabilities – Despite decades of investment in backup, enterprises have not built systems resilient enough for modern threats.
- Data sprawl – The sheer volume and distribution of data across on-prem, cloud, and edge environments makes coordinated recovery extremely complex.
- Smarter adversaries – Attackers are leveraging AI and automation to target not just production systems but the backups themselves, ensuring deeper impact.
- Process and people constraints – Recovery is not just a technical challenge; it requires orchestration across teams, governance, and compliance mandates that often slow response.
Implications for the Market
In our view, this is both a crisis and an opportunity. For enterprises, the inability to recover mission-critical data at scale exposes existential risk. For vendors, this represents a massive market opening: the evolution of traditional backup into true cyber resiliency platforms. The shift will require blending high availability, cloud-native recovery, immutable storage, and even traditional mediums like tape into a unified, intelligent architecture.
We believe the organizations that close this gap—those that can guarantee rapid and near-complete data recovery — will be the ones that earn the trust of boards, regulators, and customers. Conversely, the current state of affairs, where the vast majority cannot claim full recoverability, is unsustainable.
The Hours of Lost Data
When we translate percentages of lost or unrecoverable data into actual time windows, the picture becomes even more sobering. The study asked respondents to identify their actual recovery point objective (RPO) — that is, how much data in terms of time they lost after a successful cyberattack. The findings reveal the real business impact in stark terms.
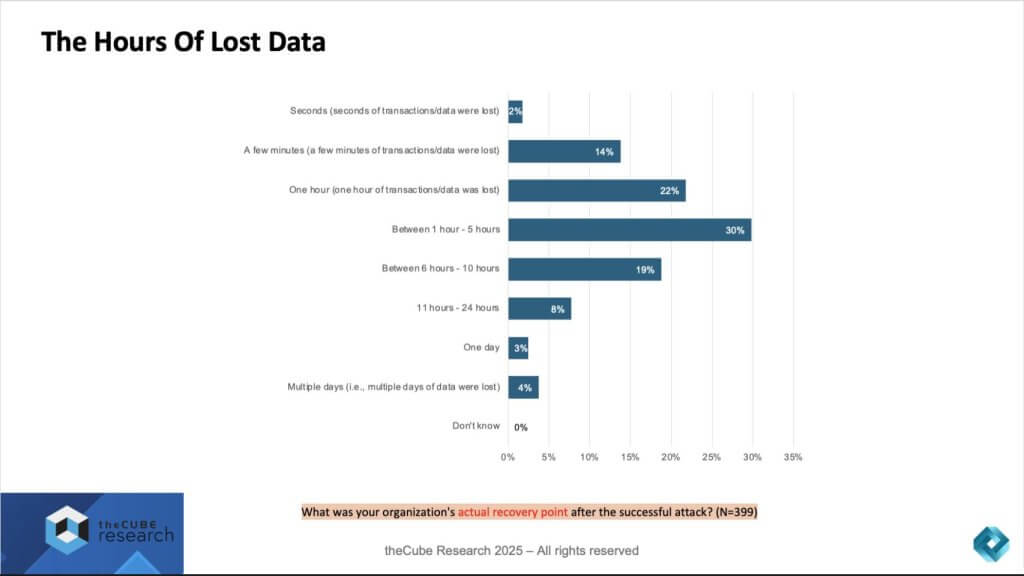
- 30% of organizations reported losing between 1 and 5 hours of data.
- 22% lost roughly one hour of transactions.
- 19% lost between 6 and 10 hours.
- Nearly 15% combined lost a full day or more of data.
Only a small fraction — about 2% — reported losses measured in seconds, which is the aspirational goal but far from the norm.
Business Impact
We believe this data illustrates a key point in that every lost hour is more than just a technical inconvenience — it’s a productivity killer, a revenue drain, and a reputational hit. In industries such as financial services, retail, or healthcare, losing even one hour of transaction data can translate into thousands or even millions of compromised records, delayed customer interactions, or compliance breaches.
Christophe Bertrand framed it well: can you imagine losing an hour of enterprise transactions? For a global business, the downstream effect is enormous. Beyond the direct operational disruption, the inability to account for or recreate lost data introduces compliance liabilities that are often more damaging than the immediate outage.
Why This Matters
In our view, these findings reinforce three critical realities for enterprise leaders:
- Zero data loss is unrealistic – The market must come to terms with the fact that true zero-loss scenarios are virtually impossible in the face of physics and low probability but high impact events.
- RPO needs to be minimized – Organizations must aim to shrink the window of loss as much as possible, especially for mission-critical systems where every minute (or second) counts.
- AI and automation will be key – From high-availability solutions to AI-driven RPO and RTO optimization, next-generation tools will be required to move closer to continuous recovery.
The gap between aspiration and reality is wide. Most organizations are still losing hours of data, and only a tiny percentage can confidently recover in near real time. This reality underscores both the urgency of the challenge and the size of the market opportunity for vendors who can deliver truly resilient, low-latency recovery solutions.
There Is No Quick Recovery for Most
The research makes one reality painfully clear – i.e. recovery from cyber incidents is not quick. On the left, when respondents were asked how long it would take them to fully recover from a ransomware or cyber incident, most indicated somewhere between 4 and 15 days. On the right, when those who had actually experienced attacks were asked how long it did take, the responses were almost identical.
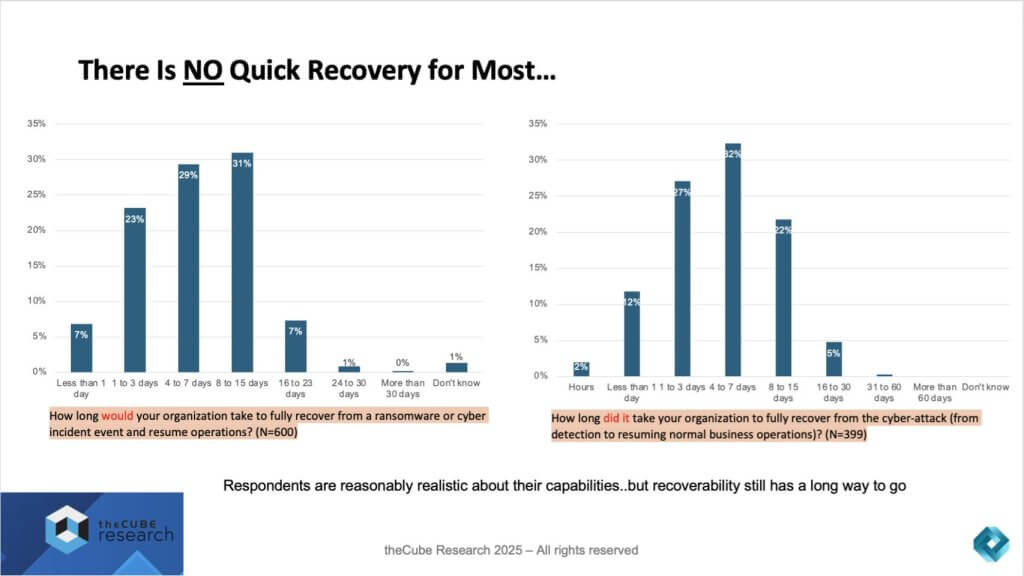
- 29% estimated recovery would take 4–7 days, and 31% said 8–15 days.
- In practice, 27% experienced 1–3 days of downtime, 32% 4–7 days, and 22% 8–15 days.
- Only a very small minority reported full recovery within a single day.
This consistency between expectation and reality suggests organizations are aware of their limitations. They know recovery takes days or weeks, and most have accepted that as the current state of play.
Business Consequences
The implications extend far beyond IT operations. When recovery consumes a week or more:
- Investments in new applications and infrastructure grind to a halt.
- Productivity is severely disrupted, with lost revenue compounding daily.
- Customer trust erodes as downtime persists and service levels degrade.
In our view, this is why cyber resilience is now a C-suite and board-level priority. Business leaders increasingly understand that resiliency is not just about getting back online — it’s about minimizing business disruption, protecting revenue, and maintaining stakeholder trust.
The Ransomware Dilemma
Another critical data point from the research reinforces why paying ransoms is not a viable strategy. The vast majority of companies that paid did not recover all their data. In fact, only about one in ten reported recovering 100% of their data.
That means ransom payments are both a poor recovery strategy and an additional financial liability. Instead, the smarter investment is in people, processes, and technologies that allow organizations to recover on their own terms.
Cyber insurance enters this discussion as well. While premiums are rising, insurers now demand more rigorous assessments of infrastructure, people, and processes before coverage is granted. In some ways, this external pressure is creating a positive forcing function—driving organizations to improve resiliency in order to qualify for coverage.
Our Take
We believe the data shows that recovery is still too slow, too partial, and too uncertain. The path forward is not ransom payments but building cyber resiliency into every layer—data, infrastructure, and people. The firms that close the gap between expectation and reality will emerge as leaders in digital trust and continuity.
Cloud and AI-Based Threats: The New Frontline
The research reveals a shift in the hierarchy of concerns for IT and cybersecurity leaders. Traditional risks such as ransomware encryption and data exfiltration remain pressing, but they have now been overtaken by cloud security (45%) and AI-driven cyberattacks (44%) as the top two issues keeping practitioners awake at night.
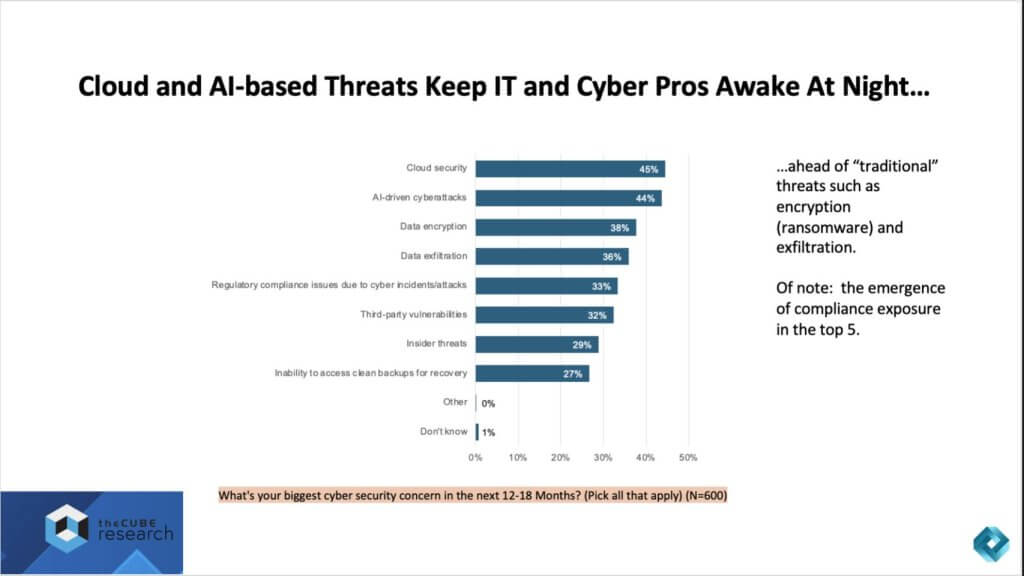
This marks a significant evolution in the risk landscape. Cloud has become the dominant operating model and, by extension, the first line of defense. Early on, many enterprises assumed that by entrusting their workloads to hyperscalers, they were absolved of much of the security burden. The reality is different: hyperscalers excel at securing their infrastructure, but the responsibility for data and applications remains squarely with the customer. That shared responsibility model is now better understood, but the survey shows it is also a source of heightened anxiety.
The Dual Role of AI: Friend and Foe
AI emerges as both a new weapon for attackers and a potential ally for defenders. Respondents recognize the duality:
- As a threat, AI is being leveraged by adversaries to automate attacks, increase velocity, and evade defenses.
- As a defense, AI offers opportunities to strengthen protection through automated incident detection, prioritization, and recovery.
We believe this ambivalence underscores the urgency for organizations to not only defend against AI-powered threats but also adopt AI in their own resilience strategies. In a sense, enterprises must fight fire with fire.
Compliance and Governance Pressures
The data also highlights the rising prominence of regulatory compliance (33%) as a top-five concern. This aligns with the growing influence of public policy and regulatory bodies in shaping enterprise security agendas. Data protection is no longer just about operations—it’s about maintaining the ability to prove compliance in the face of increasing scrutiny.
What This Means for the Market
Our research indicates that the convergence of cloud responsibility, AI disruption, and compliance pressure is reshaping the cybersecurity agenda. The organizations that succeed will be those that:
- Accept ownership of their data regardless of where it resides.
- Invest in cyber resilience that includes SaaS, hyperscaler, and private cloud workloads.
- Leverage AI responsibly to enhance defenses while preparing for AI-enabled attacks.
- Elevate governance and compliance as integral components of their resilience strategy.
In our view, this dynamic is ushering in a new leadership paradigm. As the sophistication of threats grows, enterprises may increasingly look to executives with deep technology backgrounds—not just sales or finance pedigrees—to lead in traditional industries. This shift reflects the reality that cyber resilience is now inseparable from business strategy.
The bottom line is cyber remains a cat-and-mouse game where the enemy grows smarter every day. The organizations that “skate to where the puck is going” will be the ones that define best practices in this next era of cloud and AI-driven security.
The Spending Picture: Data Protection Horses on the Track
The ETR spending data gives us a real-time view of how the pure-play data protection vendors are positioned. This cut excludes multi-segment vendors like Dell, since the taxonomy groups them in broader storage, but it’s still a telling snapshot of the competitive landscape.
The Y-axis shows net score, a measure of spending momentum or velocity. The X-axis represents account penetration — a proxy for market presence. The red dotted line at 40% is the bar for highly elevated spending momentum.
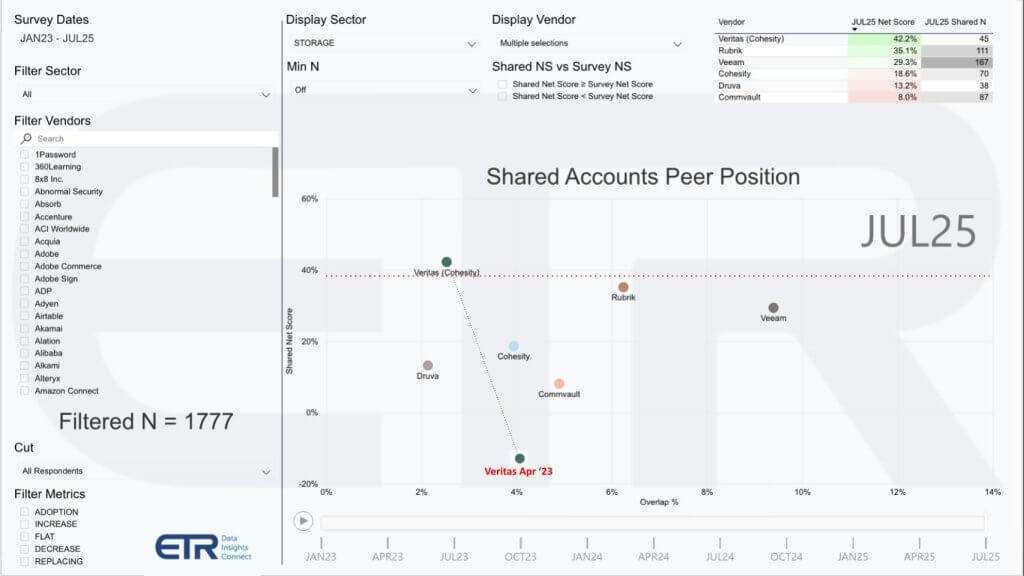
Key Observations:
- Veritas (Cohesity) – The standout story. A year ago, Veritas was a laggard, but post-acquisition by Cohesity, it has staged a dramatic rebound, leaping to the top of the peer set with a 42% net score. Even with a smaller sample (45 accounts), the trajectory is undeniable. This suggests Cohesity has not only stabilized Veritas but reignited momentum, particularly in large enterprises.
- Rubrik (35%) – Bipul Sinha’s pivot to a cyber-first identity has proven prescient. While initially viewed as an overpivot, the data shows it worked. Rubrik is benefiting from being perceived as a cybersecurity company first, and the market is rewarding that focus.
- Veeam (29%) – Strong on the X-axis due to deep penetration, especially in the midmarket, but its net score momentum is more muted compared to peers. Veeam remains highly efficient, with an enviable marketing engine, but the enterprise story is still developing.
- Cohesity (19%) pre-Veritas – Before the Veritas deal, Cohesity’s standalone position was not as prominent. The acquisition now looks like a masterstroke by Sanjay Poonen, bringing scale and credibility with the largest global firms.
- Druva (13%) – Still in the mix, but further down the momentum scale. Its SaaS-native positioning resonates, though it lacks the scale of the leaders.
- Commvault (8%) – The weakest in this peer group. Its net score has dropped nearly 20 percentage points over the past year, raising concerns about competitive positioning and long-term momentum.
Interpreting the Market Dynamics
Our research indicates three big takeaways from this data:
- M&A as a Catalyst – Cohesity’s acquisition of Veritas shows that not all M&A destroys value. In this case, it appears to have stopped defections and reignited enterprise momentum.
- Cyber Positioning Wins – Rubrik’s pivot to cybersecurity, while risky, is paying off. Competitors are now following that playbook.
- Scale Matters – As Christophe Bertrand noted, getting to $1.5–$2B in revenue is becoming table stakes. Vendors lacking scale—like Druva and Commvault—may struggle without consolidation or deeper ecosystem ties.
Looking Ahead
We believe the next big differentiator will be how vendors operationalize AI as a friend rather than a foe. Those that can embed AI into cyber resiliency, recovery, and data protection workflows will separate themselves from the pack. In our view, the market is heading toward further consolidation, with ecosystem breadth and AI capabilities dictating who emerges as the long-term winners.
Wrapping Up: The Hard Truths of Cyber Resiliency
After walking through the survey data and spending trends, several hard truths emerge that frame both the magnitude of the challenge and the opportunities ahead.

First, cyber-resiliency is not just a technology issue—it is a business imperative. The evidence shows that data-related risks translate directly into financial loss, operational disruption, compliance failures, and reputational damage. This is no longer an IT silo problem; it’s a systemic challenge that touches every part of the enterprise.
Second, most organizations remain dangerously exposed. The survey revealed that mission-critical applications are not fully recoverable in most firms, vast amounts of data are permanently lost in attacks, and recovery stretches into days or weeks. Weak links exist across every layer of the infrastructure, from backups to SaaS to AI workloads.
Third, the vendor landscape is shifting. The boundaries between backup, recovery, cybersecurity, and compliance are blurring. Vendors are converging around cyber-resiliency as the unifying theme. Some, like Cohesity with Veritas, are using M&A to achieve scale and credibility. Others, like Rubrik, have successfully repositioned themselves as cybersecurity-first players. Meanwhile, scale pressures and the need for AI integration are likely to accelerate consolidation across the sector.
Finally, there is no AI without cyber-resilient data. Organizations rushing to deploy AI initiatives must reckon with the quality, compliance, and recoverability of the data feeding those models. Cyber-resilient and compliant data is the prerequisite for trustworthy AI at scale. Without it, AI projects will fail to achieve ROI and could even exacerbate risk.
Our Recommendations
Based on the data, our research indicates five imperatives for enterprises and vendors alike:
- Elevate cyber-resilience to a board-level priority. Treat it as a business continuity and revenue-protection strategy, not just an IT control.
- Strive for near-total recoverability. Anything less than 100% protection for mission-critical apps introduces unacceptable business risk.
- Close the alert fatigue gap with AI. Adopt automation and AI-driven incident management to ensure critical alerts are not ignored.
- Demand interoperability from vendors. Security, backup, and governance tools must integrate seamlessly; siloed products create vulnerabilities.
- Anchor AI initiatives in resilient data. Use the NIST framework as a baseline to evaluate vendor claims and ensure compliance, governance, and resiliency are built in.
The Bottom Line
The market is at an inflection point. The volume and velocity of cyber threats, amplified by AI, are growing faster than traditional defenses can handle. Enterprises must shift from a reactive posture to a proactive, integrated resilience strategy. Vendors that can converge backup, security, and governance—while embedding AI—will shape the future of this market.
In our view, the defining competitive advantage in the age of AI will not simply be who can build the most advanced models, but who can secure, govern, and recover the data that fuels them. Without cyber-resilient data, there is no AI.