CISA’s Secure by Design Pledge is a voluntary pledge that enterprise software vendors make in a good-faith effort to set and attain certain security-focused goals, the most fundamental of which is to build cybersecurity into the design and manufacture of tech products. This pledge includes on-prem software, cloud services, and Software-as-a-Service (SaaS), in addition to enterprise software products and services. I read an article from Dark Reading calling the pledge toothless and basic, but the reality is that it’s a start. In my view, a much-needed effort to make security foundational as a part of product development.
RSA Attendees Opt in to CISA’s Secure by Design Pledge
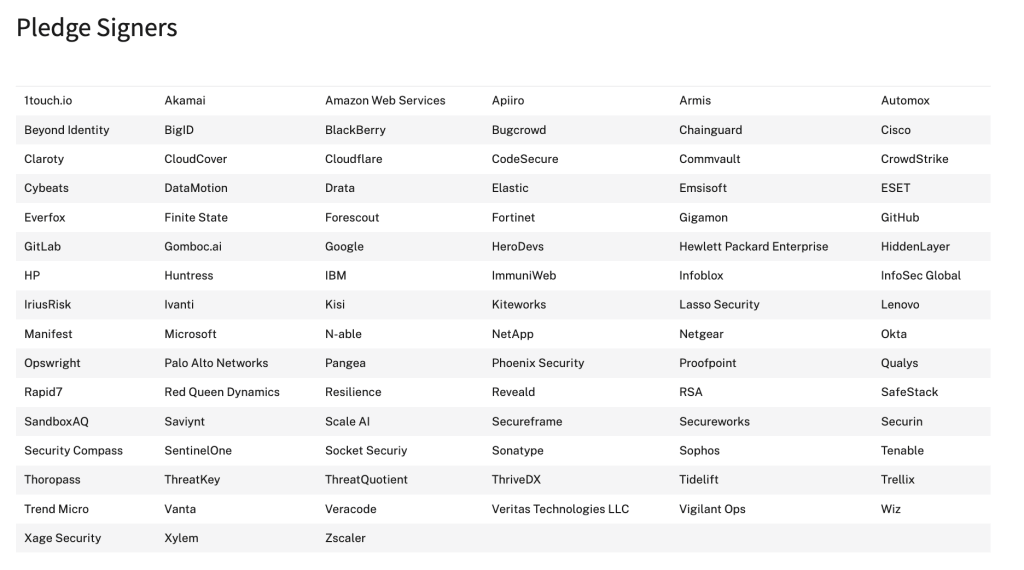
At RSA last week, CISA’s Secure by Design Pledge was a topic of discussion. Today, about 68 companies have signed the pledge, committing to bake-in security from the early design stages, continuing throughout the product lifecycle. Some of the signors of the Secure by Design Pledge include Cisco, IBM, CrowdStrike, Microsoft, AWS, Google, Zscaler, Palo Alto Networks, Fortinet, Okta, HP, Netgear, Okta, Akamai, SentinelOne, Cloudflare, Scale AI, Elastic, NetApp, HPE, Secureworks, Sophos, InfoSec Global, Trellix, Wiz, RSA, Proofpoint, and Qualys. See the full list of Secure by Design pledge signers here:
CISA’s Secure by Design Pledge: Toothless or an Important Step Forward?
CISA’s motivation with the Secure by Design Pledge is understandable: if vendors embrace security as a foundational element of product design and development, it reduces the need for government intervention, policy, and beyond. It’s a total transparency play here and a “we’ve gotta start somewhere” moment, and I am down with that. It’s also a smart move when vendors step up and acknowledge that change needs to happen and commit to participation rather than waiting around for the government to mandate change.
CISA, America’s Cyber Defense Agency, has laid out seven goals that manufacturers can work toward, and making the pledge means that participants can also get suggestions on ways to not only accomplish the goals they’ve set, but also insights on how to measure progress along the way.
The Seven Goals of CISA’s Secure by Design Pledge
The seven goals of CISA’s Secure by Design Pledge, and within one year of signing the pledge, signors commit to:
- The reduction of default passwords in products
- An increase in the use of multi-factor authentication in products
- Increase the pace of installation of patches by customers
- Reduce one or more of entire classes of vulnerabilities
- Develop and publish a vulnerability disclosure policy (VDP) authorizing product testing by the public. This policy also includes a commitment not to pursue legal action against anyone attempting to follow it in good faith. It also allows for public disclosure of suspected vulnerabilities following best practices standards and provides a method, or channel, for reporting vulnerabilities
- Embrace and demonstrate transparency in vulnerability reporting by including Common Platform Enumeration (CPE) and Common Weakness Enumeration (CWE) fields in every CVE product record and, when it comes to high-impact (and critical) bugs, a commitment to issuing those CVEs in a “timely” manner
- Providing ease of discovery for customers to find evidence of cybersecurity intrusions that might affect their products
It’s important to note that these commitments to CISA’s Secure by Design Pledge are voluntary, and there’s no real mechanism to determine which signors of the pledge are adhering to these goals, but to my way of thinking, it’s at least a step forward and an attempt to make security foundational in product design and development — and that’s as it should be.
Security as a Foundational Part of Development and Product Lifecycle Helps Everyone
More secure software is good for everyone. It protects critical infrastructure. It protects against data breaches and data exfiltration, and it protects end-user customers who largely rely on vendors to get it right, do the right things, and provide products that are safe. That’s especially important today, when our homes, offices, and lives are filled with endpoints: routers, smart TVs and appliances, webcams, children’s toys, printers, robots, connected vehicles, smart cities and buildings, medical devices, the list goes on. More endpoints mean an increased attack surface and infinitely more opportunities for threat actors and more risk for users.
While the Secure by Design Pledge is not legally binding and certainly depends on the signors to make some forward progress on this front, recognizing that there’s a problem and working toward a solution is infinitely better than the status quo. I’m here for it.
If you’re interested in learning more about the Secure by Design Pledge, email the team at CISA for more information.
Check out more of our RSA Conference 2024 coverage here:
RSAC 2024 Goes Beyond AI-Powered Security to Securing AI Itself
ETR Survey Findings on Security Spending Play Out on RSAC Show Floor
IT Security Spending Keeps Rising Amid Gen AI Threats: Analysis from theCUBE at RSAC