Long Read: If you look closely enough, risk lurks in every corner of every organization. Overwhelmed security teams often struggle to keep pace with the rate at which the groups they are tasked with protecting are deploying software and generating data, a challenge made exponentially larger by AI.
If that weren’t enough, malware, phishing, ransomware, third-party risk, vendor risk, and even insider threats form a mountain of risk that can seem insurmountable, for even the largest enterprise.
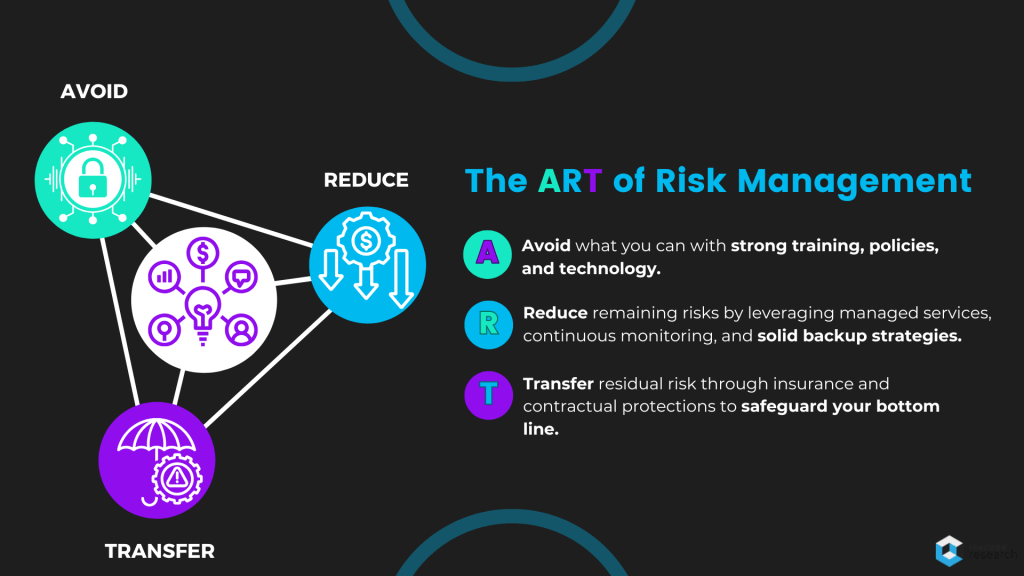
While the challenge is daunting, the good news is that risk management essentially boils down to three strategies that can be used as a simple framework.
The ART of Risk Management: Avoid, Reduce, and Transfer.
The rate of change in technology makes it nearly impossible to write a policy that covers all foreseeable circumstances. By assessing both the risk of each new project/software/vendor itself, as well as the options for applying ART, organizations can make tactical decisions as new technologies and threats emerge, remaining agile within an easily understood framework.
Here’s what ART looks like in security.
Avoid
Risk Avoidance involves taking proactive measures to prevent or mitigate risk (cyber incidents) before they occur. By eliminating the risks, you minimize the likelihood of a security breach or outage ocurring in the first place.
🎓 Training
Data Literacy
Few organizations take adequate steps to ensure every employee who creates, processes, or stores data understands how data should be categorized, where those categories of data can be stored, and how long the data can be held before deletion.
Employee Awareness
Phishing attacks remain one of the most common vectors. Regular security awareness training helps staff recognize suspicious emails, links, and potential insider threats.
Role-Based Education
Employees handling sensitive data, such as those in finance or HR, may need more specialized training on handling personally identifiable information (PII) or financial data.
💻 Technology
Protection
Effective endpoint, cloud, and network protection help stop problematic traffic and activities at the point of entry, but these technologies only work if they are properly deployed, configured, and maintained.
Ongoing Management
A few often overlooked, but critical risk avoidance strategies include system hardening, which helps to remove unnecessary services, applications, and default settings that are commonly exploited, and patch management, which keeps software, operating systems, and devices up to date.
Identity and Access Management
Last on the technology front, strict access controls and policies, including least-privileged access, multi-factor authentication (MFA), and zero trust help prevent one compromised device from turning into an incident.
By focusing on training people, eliminating unnecessary technology, and enforcing strong policies, organizations can avoid a significant portion of common threats.
Reduce
Even with the best preventive measures, risks can’t always be completely avoided. Risk Reduction strategies aim to limit the impact of a successful attack and minimize the resulting damage or downtime.
👥 Talent
Leverage Managed Service Providers (MSPs) and Managed Security Services Providers (MSSPs)
Many organizations evolve with IT and Security in-house. A large portion of these companies would be better served by leveraging a more experienced third-party. MSPs don’t just fix issues as they arise; they monitor and update systems consistently, reducing or avoiding vulnerabilities. For more complex needs, MSSPs focus specifically on cybersecurity, managing firewalls, SIEM, endpoint/network/cloud detection, and 24/7 threat monitoring. In an incident, MSSPs provide professional responders and threat intelligence, enabling a faster, more structured response.
💻 Technology
Resiliency through Segmentation
If attackers compromise one part of your network, system, or account access, segmentation can prevent them from moving laterally to more critical assets.
Robust Backup Strategies
Regular, secure backups (ideally stored offline or in a separate cloud with strong encryption) can drastically reduce downtime if ransomware or data corruption occurs.
Security Monitoring and Penetration Testing
Whether in-house or via an MSSP, continuous security monitoring can spot anomalies before they become catastrophes. Regular tests reveal weaknesses so you can fix them proactively.
For many organizations—particularly SMBs—partnering with MSPs and MSSPs offers an affordable and high-impact way to reduce risk. By offloading specialized tasks to professionals, your team can focus on core business functions while gaining peace of mind.
Transfer
Transferring risk involves shifting some or all of the operational and financial burden of cyber risk to a third party. Although it doesn’t eliminate risk, it can help organizations recover more quickly and minimize financial impacts if a breach occurs.
🧑💻 People
Outsourcing High-Risk Functions
If a function is too costly or complex to secure in-house, outsourcing it to a specialized provider who bears the risk can be a strategic move.
📑 Policies
Cyber Risk Insurance
Cyber insurance covers costs such as legal fees, breach notifications, data recovery, and even ransom payments in some (increasingly rare) cases. Underwriters often require proof of security controls, so adopting strong avoid and reduce strategies can lower your premiums.
Umbrella Coverage by Service Providers
Some managed service and security providers offer umbrella coverage or warranty-like assurances as part of their service packages. Bundling coverage with managed services can be more affordable than purchasing standalone cyber insurance, especially for SMBs with limited budgets.
Contractual Agreements & SLAs
Transferring risk can also involve negotiating strong service-level agreements (SLAs) with vendors or MSPs, who assume defined liability in the event of certain failures.
While transferring risk doesn’t absolve an organization from implementing foundational security controls, it can prevent catastrophic losses and preserve business continuity when preventive measures fail.
What’s the Angle?
By combining these three strategies, organizations can create a robust, layered defense capable of withstanding modern cyber threats. Not every threat can be avoided, and not every incident’s impact be fully contained, but by taking a balanced approach, you can protect your business, maintain customer trust, and ensure that a single attack doesn’t derail your organization’s long-term success.
Additionally, a simplified framework helps the rest of organization, as well as the executive team and board, to document and analyze risk, as well as accept that if there is no plan in place to avoid, reduce, or transfer risk, an organization is choosing to accept the risk. This helps to protect the security team from bearing the brunt of incidents arising from decisions they had no awareness of and/or influence over.



