Premise
Enterprise IT has been ignited by the Digital Economy and exploded into thousands of users, devices, applications and questions: When users are using their laptop over coffee-house wifi to look up a customer on their public cloud SaaS CRM system, before logging into email on-premises to send an invite to the customer: are they using one identity, or two? Without a single, unique trusted identity across hybrid cloud, there is no hybrid cloud because it looks like a discombobulated and fragmented set of “stuff” to the user, whether that’s an infrastructure administrator or a business administrator. This pounding headache has to be addressed with modern hybrid identity systems.
Content
- The digital economy and the drivers for modern hybrid identity systems.
- What modern hybrid identity systems need to do for the hybrid cloud.
- Examples of modern hybrid identity systems.
- Final thoughts.
1. The digital economy and the drivers for modern hybrid identity systems
The experts on the interplay between the digital economy, the second machine age, platforms and the technology landscape reveal that technology is disrupting the enterprise.
Disruptive platform plays, as explained by MIT’s Marshall van Alstyne, are happening everywhere: public cloud players have built multi-billion dollar businesses with demand-side, consumer-focused platforms that others build value on top of.
The five drivers of hybrid identity are:
1. Enterprises, such as Royal Phillips, are rejecting the traditional model of IT. Their VP Technology, Alan Nance, described the “end of the enterprise agreement and the start of the consumption cloud”. This is about more than just buying infrastructure in a different way: it changes the way IT is consumed, giving Royal Phillips new modes of experimentation and learning; it changes the way IT is controlled, with a particular impact on system-wide controls such as identity and access management.
2. Identity is your unique passport in the enterprise, without it you can’t work and the business won’t function. Do it badly and there is a direct impact on the things that business cares about: innovation and productivity (difficult systems lower productivity), brand (security breaches impact brand), and costs (many disconnected, niche identity systems are not cheaper than one unified system).
3. Users should not be exposed to the churning underbelly of IT. Users are consumers and customers in this age of the demand-driven platform, and they have expectations of service: simplicity and ease of use, beauty and design. They have used authentication systems from Google, Twitter and LinkedIn and they expect the same level of self-service and ease of use in the enterprise.
4. IT can not cope without a hybrid identity system. The rate of change and complexity of users, devices and applications means that without federated and self-service systems, without better intelligence and policy enforcement, IT will be inundated with tickets and calls and security will fail.
5. We are living in the age of cyberwarfare and hybrid cloud exposes a larger surface area of attack. Old, private, internal systems are not cloud native: use an enterprise-friendly, cloud-friendly, app-friendly and user-friendly system. It has to be easy to consume, easy to deliver and operate, and be ubiquitous and consistent to be effective.
Hybrid clouds are the new mix of on-premises and off-premises systems at all layers of infrastructure and applications: this isn’t just the slice of apps, or users, or devices, or infra; it is about the whole pie. It is likely that one user uses many slices of this hybrid cloud pie:
There is no such thing as a hybrid cloud without hybrid identity. If you don’t have a hybrid identity and access management system then you don’t have a hybrid cloud, or at best a pretend version of one.
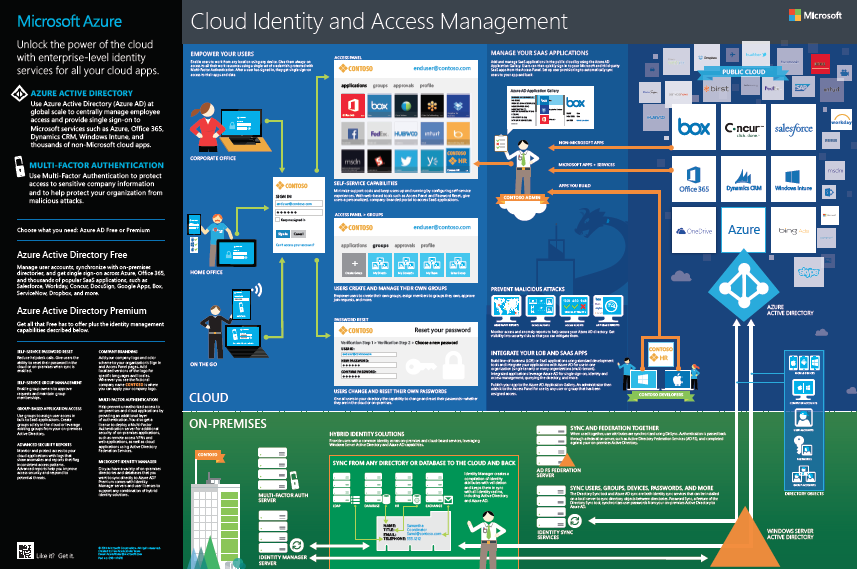
Microsoft are just one of the hybrid cloud identity players, and they have a nice infographic that shows the scope of a hybrid cloud solution:
2. What modern hybrid identity systems need to do for the hybrid cloud
Identity and access management is as old as IT itself but the hybrid cloud needs a modern identity system.
|
One identity, many services |
The same identity should be used for all systems, from on-premises to SaaS, and this requires techniques such as federation, syncing, use of authentication protocols and more. |
|
Self-service |
Users should be able to self-register to an approval process in the identity system. Application access and password resets are all self-service. |
|
Single Sign On (SSO) |
Use of applications should be as friction-free as possible, so users should have an SSO system to propagate their logon |
|
Device Management (MDM) |
Users don’t just have a desk-based PC: they use phones, phablets, tablets and laptops, and these can be linked to the identity via Mobile Device Management systems. |
|
Multi-factor Authentication (MFA) |
Use the same multi-step authentication procedure. This is important in today’s era of malware which is the biggest source of enterprise security breaches today |
|
Proxy service |
Provide remote access to on-premises software (opposite of on-premises to cloud based). |
|
Available anywhere |
Enterprises can prefer a cloud based (but federated to on-premises, ie. Hybrid) identity service especially if they are a global company with many off-site employees. |
There are also numerous “back end” requirements of governance, auditability and intelligence which are crucial to modern identity systems. For example, there are some advanced systems that use intelligence algorithms to detect unusual user access behaviour, such as accessing the system from a different country or timezone.
Bring your own ID (BYOID) is a faltering concept of letting users bring a previously approved ID into the enterprise, such as their social media, 3rd party or government approved identity. Prevailing thought is that this hasn’t worked due to lack of trust between enterprise and 3rd parties. Even government-approved falters when an enterprise is global. This is also an age of Snowden and zero trust so there is little near-term hope for this approach.
All of these hybrid identity features benefit the user and the administrators, here are some real situations that can be avoided by using a single, hybrid identity system in your hybrid cloud:
- One user, many identities: If a user has more than one identity then they will deal with that complexity by having easy to remember credentials which makes them a weak link for hackers, vulnerable to email-based malware.
- Many apps, many systems: If applications have separate identity systems then it becomes a manual job to maintain the integrity of the identities on that system for events such as staff changes (on-boarding, job change, leaving).
- Complexity and fragmentation = entropy. A fragmented identity system leads to fragmented accountability, with untrusted devices allowing suspect users to identify unapproved applications all of which the enterprise is implicitly approving of and responsible for.
3. Examples of hybrid identity systems
The identity and management discipline is decades old and it is going through a resurgence because of the impact of the digital economy, cyberwarfare and IT entropy risks. This means there are new market entrants and traditional tech titans all playing in the spaces with varied offerings that must be carefully matched to an enterprise needs. This list isn’t exhaustive, or in any particular order, but represents the most commonly discussed .
Notes:
- Some other technology vendors have partnerships with specialist providers, so the player list is considerably longer than this and the market is somewhat complex.
- There are some Identity and Access Governance (IAG) products that are excellent and deep on-premises solutions but they are not hybrid friendly; conversely Identity and Access Management (IAM) services might not have such deep features as IAG products, but they span the hybrid cloud model and fit better. Trust IT to have such complex terminology.
4. Final thoughts
Transition from a legacy identity system, or from many unconnected identity systems, to a modern hybrid identity system might seem to be a daunting task because it is such a core part of the IT landscape, but it isn’t an optional one. Don’t listen to vendors who can’t deliver in this space who say that this isn’t important, or use Fear, Uncertainty and Doubt to cloud the issue. There are so many complexities in today’s landscape when looking at the plethora of users, devices and applications in the face of the irrepressible digital economy and in the shadow of cyberwarfare that hybrid identity systems are a must for all enterprises of all sizes. An enterprise’s applications, data and people are the business, and if you don’t have a hybrid identity system, then you don’t have a hybrid cloud.
Take the end users perspective when it comes to identity: Where there is simplicity and ease of use, there is cohesion, trust and security.
Action needed: People and complex systems make a weak link in security so make hybrid identity the core of your hybrid cloud journey and secure your people, applications and devices.