Organizations continue to spend more on security with 87% of firms expecting to increase spend on cyber in the next twelve months. But are we safer?
It’s estimated that firms on average have between 60-75 security tools installed. While leading vendors logically market the benefits of addressing tools sprawl and complexity through consolidation, the data suggests that more than half the firms are increasing the number of security vendors installed with a very small percentage able to affect vendor consolidation. Adding to the challenge is an environment where SecOps pros have too many priorities to manage, ranging from identity, vulnerability management, patching, endpoint, SIEM, AV, zero trust, cloud security and more. Finally, firms are investing in AI to relieve the crushing labor burden security analysts face, but at the same time are being forced to balance innovation with the daily battle.
In this Breaking Analysis we preview RSA 2024 with our colleague Erik Bradley of ETR. We’ll provide a detailed analysis of a recent survey conducted by ETR, perfectly timed ahead of RSA.
Security Budgets are On the Rise
The chart below shows data from the most recent ETR survey we referenced at the top. As you can see the N is 321 respondents and the vast majority, 87% are increasing spend on security with 70% expecting an increase of 5% or more, which is higher than overall IT spending average of 3.4%. The other notable callout is that 0% of the Fortune 100 and S&P 500 respondents in the survey expect a decrease in budget.
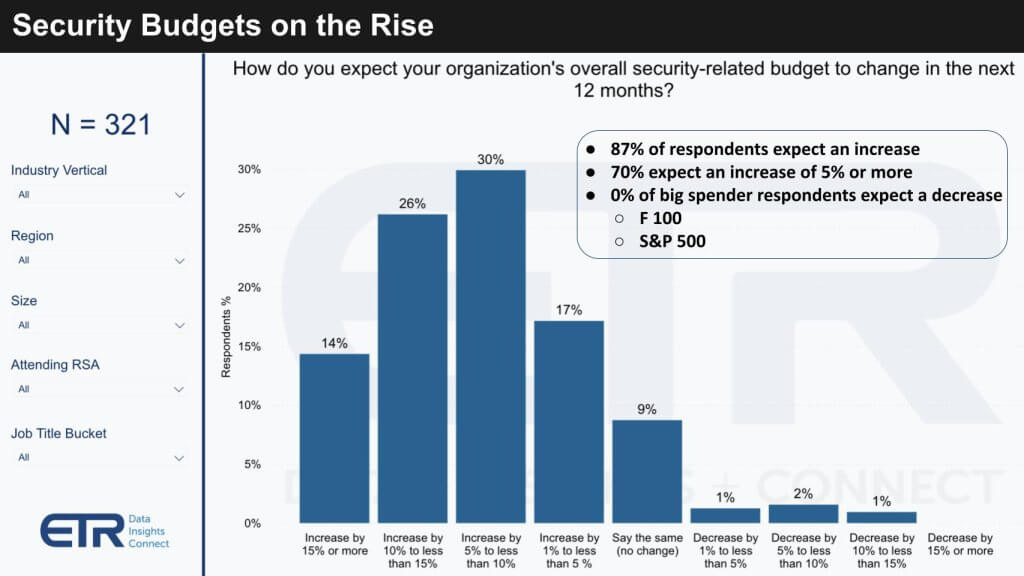
This data represents a standout revelation from the survey in that 70% of customers see their security budgets growing by 5% or more, a strikingly high rate of security spending compared to IT spending at large. The data further shows that more than half of the surveyed firms are increasing their security investment by 5% to 14%. Notably, an astonishing 14% of respondents are engaging in what we classify as ‘hypergrowth’ in spending, exceeding a 15% increase. This hypergrowth threshold is not strictly defined and could include some very large outliers, which leads us to believe that the actual figures may be significantly higher than reported.
Our analysis further identifies a notable trend within organizational size dynamics. Mid-sized companies, which ETR categorizes as those with 200 to 1,200 employees, have 92% of respondents reporting spending increases, and an exceptional 23% of them are anticipating hypergrowth. Conversely, the Global 2000 companies exhibit the least propensity towards hypergrowth, which is a rational trend given their already substantial budget baselines. This disparity underscores that the rate of security spend escalation is not only surpassing general IT expenditure but also varies by company size.
Multi-Cloud & Ransomware are Big Drivers of Spending Increases
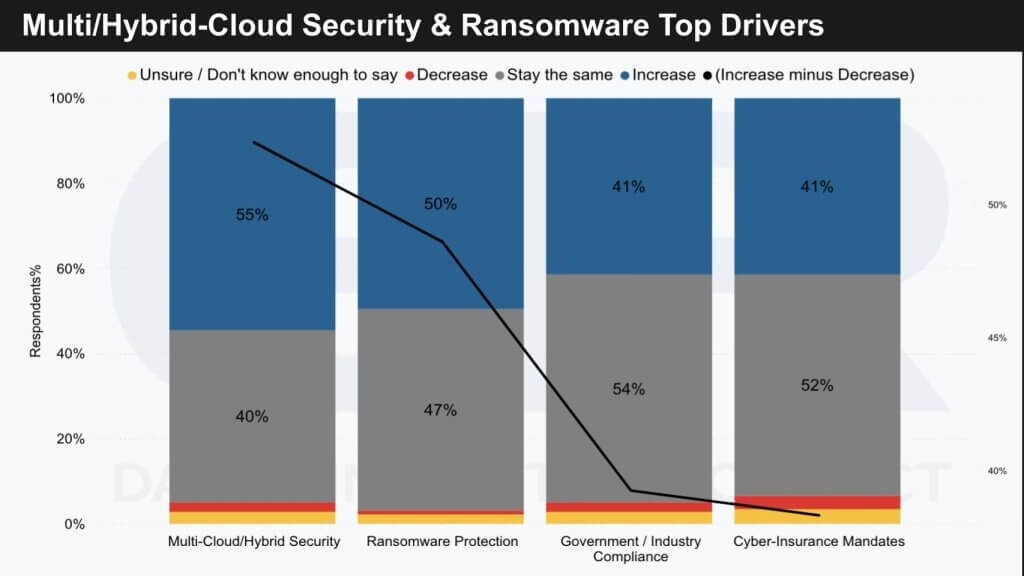
The data above shows the areas driving the highest increase in spend. Note the data is presented on a double Y axis so that black line, which is the percent of respondents increasing spend minus the percent decreasing spend is actually quite high on the right hand vertical axis.
Respondents in the ETR survey indicate that multi-cloud and ransomware are pivotal factors influencing the increase in security spending. We’ve noted in previous Breaking Analysis and supercloud research the complexity brought on by the need to secure multi-cloud and hybrid cloud environments, which inherently expand the threat surface. This complexity appears to be a substantial driver due to the increase in attack vectors it presents.
We note the following key catalysts for heightened security expenditure are:
- Multi-Cloud and Hybrid Cloud: As enterprises continue to diversify their cloud infrastructure, security spending follows suit to mitigate the risks associated with these more complex environments.
- Ransomware Protection: With ransomware consistently posing a significant threat, it remains a top priority for organizations, potentially explaining the surge in security budgets.
We further emphasize:
- Hybrid Cloud’s Momentum: Consistent with our previous discussions, hybrid cloud is identified as a current driving force. While public cloud growth showed a period of of deceleration, AI appears to be a new tailwind which will further exacerbate the adoption and need to remain vigilant when connecting to on-prem assets.
- Security Ramifications: There are implications for security models and spending due to the hybrid/multi-cloud trend. Specifically as Gen AI adoption grows, privacy, compliance, data protection and other legal concerns will escalate.
Interestingly, cyber insurance is seen as less of a driver for increased security spending, particularly within the Global 2000:
- We’ve seen a decline from 41% in previous surveys to 25% in recognizing it as an increased spending driver, suggesting a maturation trend within the cyber insurance market.
This perceived maturation perhaps is the result of a rationalization within the industry after years of tumult, reflecting a better alignment between cyber insurance demands and the realities of security tool efficacy.
Consolidate to Simplify Right? Not So Fast…
This next set of data is eye opening. The survey asked respondents whether over the next twelve months they expect the number of security vendors to increase, decrease or stay flat. The prevailing narrative in the industry would suggest that most customers are consolidating the number of vendors in their security stack. They’re not.
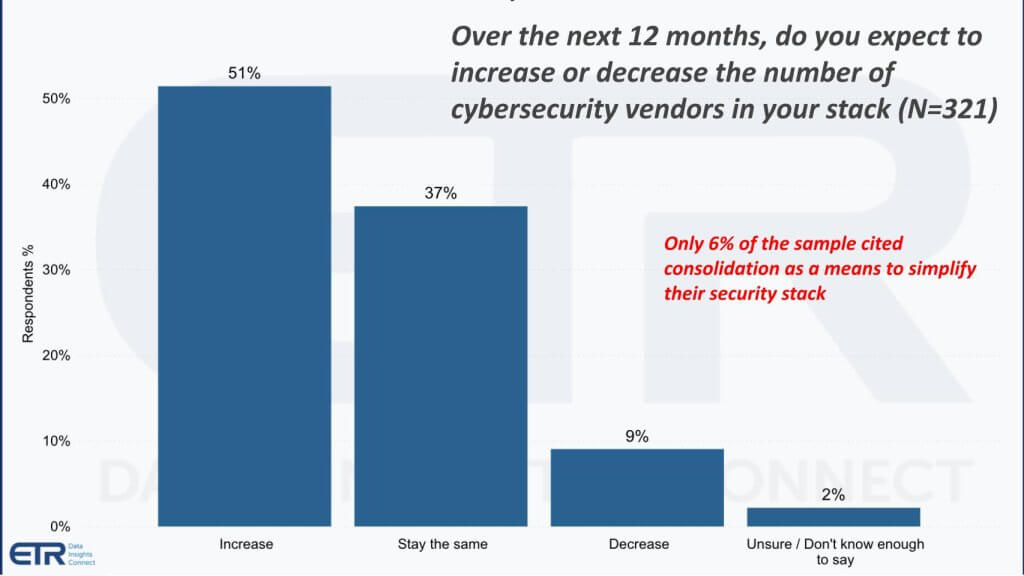
Our research reveals a significant deviation from the vendor narrative regarding security tool consolidation within organizations. Contrary to the successful examples by leading security firms like CrowdStrike, Palo Alto, and Zscaler, the data does not primarily reflect a trend towards vendor consolidation. Key findings include:
- A whopping 51% of respondents expect to increase the number of vendors in their security stack over the next twelve months.
- A mere 9% of organizations report a decrease in the number of security tool suppliers, with only 6% achieving this through consolidation efforts.
These insights lead us to anticipate:
- Increased Complexity: The data suggests a trajectory towards greater complexity in tools sprawl rather than simplification.
- Widening Skills Gaps: More vendors means more tooling and greater complexity, further pressuring organizational skills.
- Greater Demand for AI: This increased complexity and lack of talent will necessitate greater adoption of AI tools to fill gaps.
This data represents a contrarian view to the industry’s consolidation rhetoric. Despite public earnings calls touting strategic shifts towards platform integration, the ground reality reflects a persistent inclination towards ‘best of breed’ solutions and a readiness to onboard additional vendors if deemed necessary.
The gap between strategic aspirations of security companies and the operational practices of end-users suggests that, although consolidation is a stated goal, the industry may not yet be ripe for such a transition. The data firmly points to a continued increase in the number of security vendors, emphasizing the need for vigilance as security architectures evolve.
What IT Practitioners See on the Ground
We posted an informal Twitter poll, to assess sentiment in the community. While half the respondents expected the number of vendors to decrease, a healthy 30% indicated they thought the number would grow. We suspect those were likely practitioners on the ground. Below we show the comment made by one IT person who said: “Decrease implies consolidations. Increase implies new entrants. I vote increase not for that binary reason, but because the amount of new entrants exceeds consolidations…”
And for effect, we’ve superimposed an impossible to read chart – that’s the point – from ETR’s Emerging Technology Survey of privately held companies. This is the security sector and you can see how crowded it is with names that are well known like OneTrust, BeyondTrust, 1Password, Nord, Wiz, Snyk, Cato, and multiple dozens of others.
The prevailing sentiment that vendor consolidation is the dominant trend in security is not substantiated by this data. Rather the opposite appears to be true and the data indicates a tendency towards the adoption of new entrants in the market rather than consolidation. This is attributed to the sheer volume of novel solutions surpassing the rate of vendor consolidation.
We note the following additional points:
- A Plethora of Early-Stage Companies: Numerous startups are hyper-focused on specialized security niches, revealing gaps that larger, established players might not adequately address.
- Potential for Consolidation and Failure: The abundance of players in the security sector indicates ripe conditions for industry consolidation or, conversely, market exits.
The sector’s dynamism and firms’ vulnerabilities support the addition of new companies. This underscores the industry’s rapid evolution and the critical need for businesses to remain vigilant and adaptable in their security postures.
Digging into Why Firms are Adding Vendors
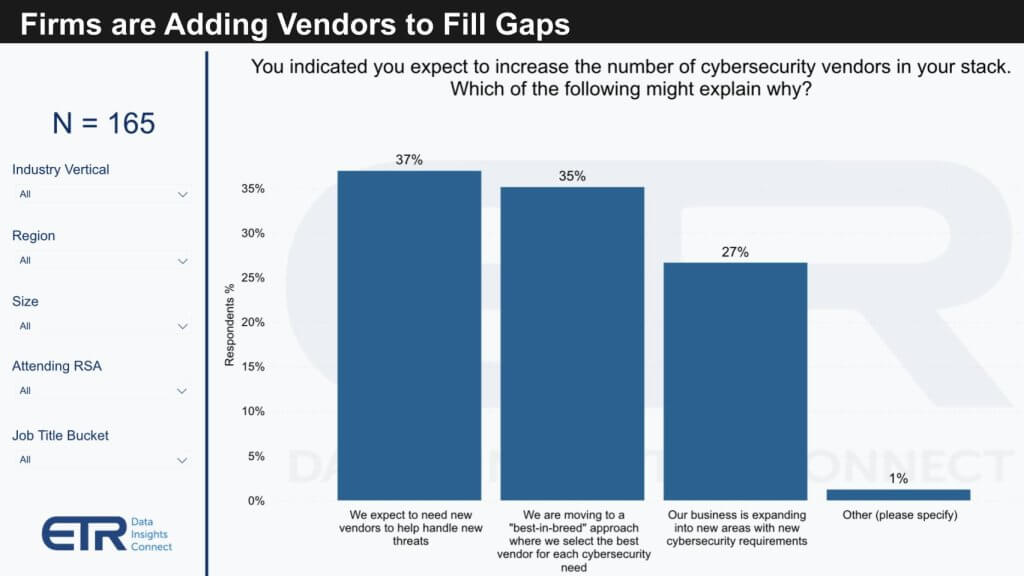
The data below drills into those respondents saying they were increasing the number of vendors in their cyber stack. The survey asks them why they’re adding vendors.
The implications are:
- Vendor Gaps: There’s an implicit acknowledgment that existing vendors fail to fill critical gaps, particularly in specialized sectors. This not only suggests a deficiency in current offerings but also signals the likely endurance of tool sprawl as a significant industry challenge.
- Specialization Over Consolidation: Despite the complexities, customers find value in specialized tools that cater to specific needs, reflecting a preference for quality and specialization over the simplicity of consolidation.
- Market Opportunity: This gap in comprehensive solutions by leading vendors paves the way for new entrants to innovate and capture market share.
There is a notable consensus that while there’s a universal preference for reducing the number of vendors, this doesn’t overshadow the demand for robust security measures. About 36% of the respondents highlighted the emergence of new threats and the pursuit of best-of-breed solutions as primary reasons for increased vendor counts. Additionally, 27% cited expanding business initiatives as a contributing factor.
In stark contrast to this trend, a small fraction of respondents—only 29 out of over 300—indicated a decrease in their security vendor stack, mainly motivated by budget constraints and a strategic push towards simplification.
We believe the discourse around vendor value and consolidation takes on greater significance in light of the term ‘spending fatigue’ used in recent earnings calls. This has sparked debate among industry leaders, with companies like CrowdStrike and Zscaler reporting contrasting trends. The question remains whether a single vendor can truly offer a best-of-breed experience across a broad portfolio, a question highlighted in discussions with other analysts on theCUBE. The emerging view seems to suggest that while ‘good enough’ might work in certain areas, in the domain of security, the stakes are too high to settle for anything less than best-of-breed, underscoring the enduring importance of a layered defense strategy.
That said, the growth and increasing ubiquity of Microsoft’s security tooling, despite the scathing report by the government’s Cyber Safety Review Board about Microsoft’s poor security practices, indicates that good enough may be good enough for many customers. Nonetheless, we believe best practice calls for layering further protections on top of Microsoft tooling.
“If You Have 10 Priorities You Have None”
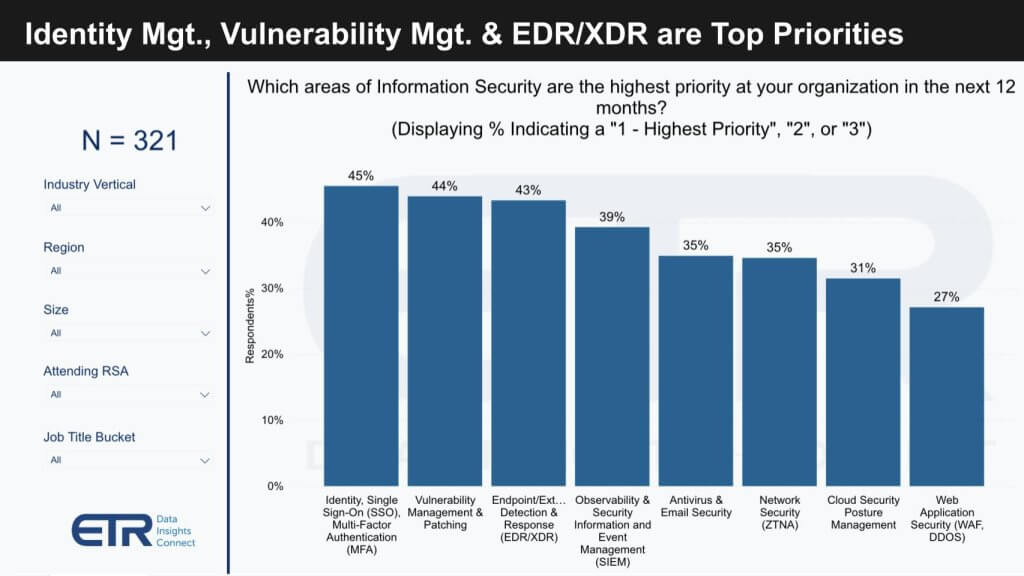
In the words of former Snowflake CEO Frank Slootman, “if you have 10 priorities you have none.” This chart below underscores the problem in cyber. You can’t narrow things down to one priority. Identity, single sign on, MFA, patching, EDR, XDR, SIEM, observability, anti-virus, Zero trust, cloud, WAF – customers face a never ending set of priorities. And if you ignore any of them, you do so at your own peril.
Our research shows that in the domain of cybersecurity, the disparity in priorities between C-suite executives and operational practitioners is becoming increasingly evident.
ETR has launched a new product, Market Arrays, which provides a deep dive into the various aspects of identity and endpoint platforms (with more sectors coming) revealing that:
- Vulnerability Management: At the C-suite level, vulnerability management emerges as a paramount concern.
- Observability and Detection: Operational practitioners prioritize observability, indicating a shift in focus towards visibility within the security infrastructure. Meanwhile, Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) have descended to lower ranks in terms of priority.
This data underscores the varying focus areas within an organization, reflecting differing priorities based on role and responsibility. It’s clear that while all facets of security are deemed critical, there’s a pronounced contrast between the strategic oversight of executives and the immediate, hands-on challenges faced by analysts. Such disparities suggest a need for greater alignment and understanding across the different organizational tiers to effectively address the comprehensive security landscape.
What do SecOps Pros Want to See at RSA 2024?
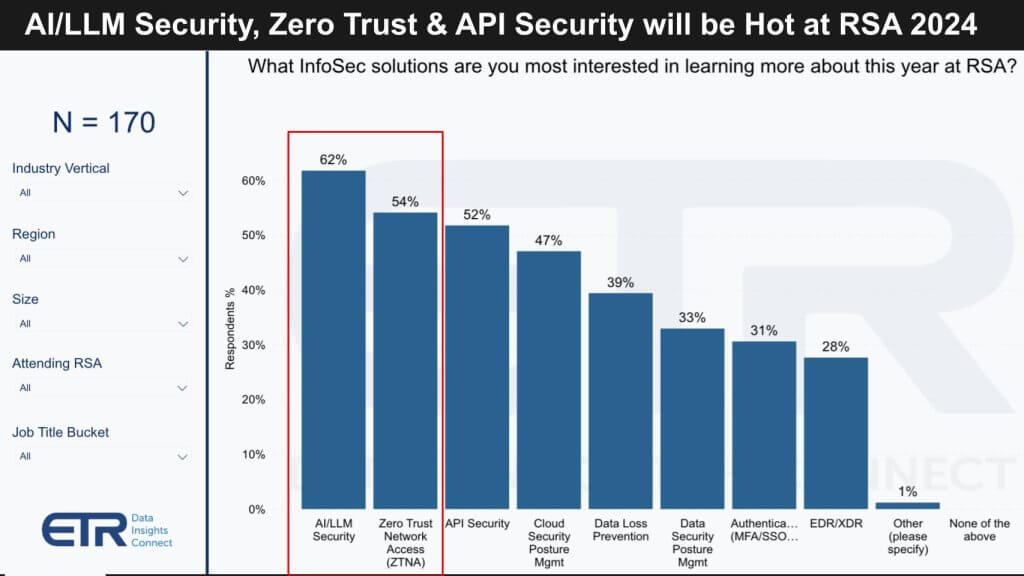
In the latest survey of 321 security professionals, 170 (53%) have indicated their intention to attend RSA. Their interests span a range of topics, reflecting the current security landscape’s complexity and the ever-growing demands on security operations professionals. The key areas of interest for RSA attendees are:
- AI in Security: A focus on the integration and implications of Artificial Intelligence in security practices.
- Zero Trust Architecture: Continuing the momentum of recent years, Zero Trust principles remain a critical area of learning.
- API Security: With its high ranking, this reflects an acute awareness of API vulnerabilities as critical points within the security perimeter.
- Cloud Posture Management: As cloud environments become more complex, managing their security posture is of paramount importance.
- Data Loss Prevention (DLP): Despite its lower ranking, DLP remains a staple concern within data-centric security strategies.
- Data Security and Authentication: These fundamental aspects continue to be a concern, especially with the evolving nature of threats.
- Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): These remain top-of-mind for addressing endpoint threats.
It is noteworthy that despite the extensive list of topics security professionals need to keep abreast of, Data Loss Prevention (DLP) and Data Security Management are surprisingly ranked lower in priority. Moreover, approximately 30% of respondents have no immediate plans to assess their data security management strategies. This could suggest a concerning complacency or a gap in recognizing the critical importance of robust data security practices amidst the fast-evolving digital threat landscape. Such findings tell us there’s a necessity for continual education and strategy reassessment to ensure comprehensive security across all organizational data touchpoints.
Double Clicking on AI Security Spending Patterns
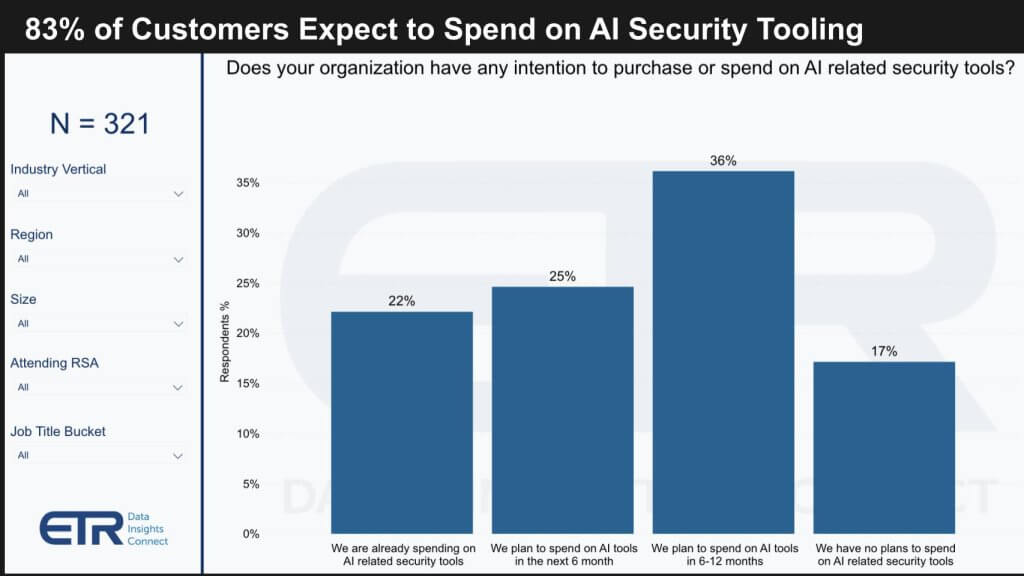
Our analysis of the latest survey data provides insights into the current and future spending trends on AI security tools. The findings suggest that AI’s role in security is expanding rapidly, with:
- 22% of respondents currently allocating budget to AI-related security tools.
- An additional 25% planning to direct funds towards such tools within the next six months, indicating a significant shift in spending patterns likely to materialize before RSA 2025.
- A notable 17% reported no plans to spend on AI-specific security tools, which could be indicative of a trend where AI is expected to be a built-in feature rather than a standalone investment.
Although a small segment indicates no planned expenditure on AI-specific tools, the broader trend highlights a substantial commitment to AI in the security domain. The intent behind question in the ETR survey was specifically geared towards net new investments in AI tools rather than incidental spending on embedded AI features within existing products.
Additional ETR data not displayed above reveals that:
- The majority (47%) currently utilize AI in only 1-10% of their security tools.
- A further 26% have AI embedded in about 10-25% of their tools.
- A smaller group, 14%, reported that more than a quarter of their security tools already incorporate AI capabilities.
These figures underscore a relatively low baseline of existing AI integration, suggesting considerable growth potential for AI application in security tools. With the majority of respondents planning to invest, the landscape of AI-enabled security tools is poised for significant growth in our view, reflecting both a demand for advanced security measures and the growing importance of AI in addressing complex security challenges, particularly the lack of qualified human labor. Moreover, as attackers increasingly use AI to penetrate organizations, AI will be of increasing importance to stop and/or detect breaches and take remedial action.
Building a Zero Trust Architecture Takes Time
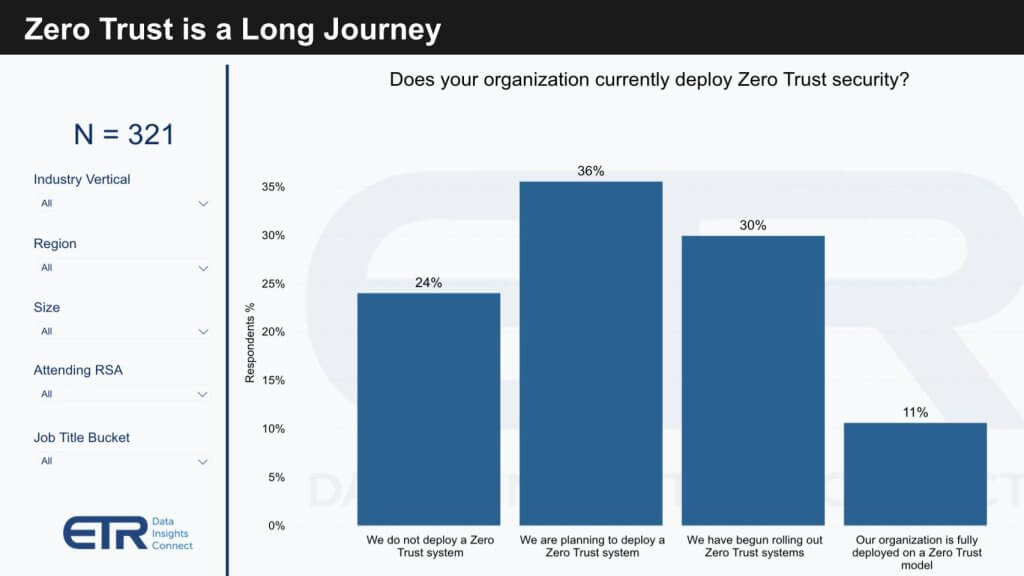
The industry narrative around Zero Trust architectures reveals a gap between market hype and the on-the-ground reality seen by security practitioners. While Zero Trust is receiving justified attention, its implementation is complex and multifaceted. Among the surveyed CISOs, there is a clear drive to adopt Zero Trust methodologies, but several hurdles remain:
- Strategic and Regulatory Alignment: Navigating the intersection of Zero Trust principles with regulatory compliance and corporate policies.
- Technical Challenges: Addressing intricate technical requirements such as micro-segmentation and ever-changing authentication mechanisms.
- Analytics: The need for robust measurement and analytics to assess the efficacy of Zero Trust initiatives continuously.
- Organizational Hurdles: The operational aspects, including funding, proof of concept stages, testing, and change management.
Despite these challenges, our findings suggest an encouraging trend towards adoption:
- Zero Trust Deployment: A surprising 11% of organizations have fully deployed a Zero Trust model, indicating progress in moving from theory to practice.
- Zero Trust Pathway: Over three-fourths of respondents are in some phase of the Zero Trust journey, either having begun the process or planning to do so.
Interestingly, there is a notable discrepancy in perceptions between job roles regarding the deployment of Zero Trust:
- Practitioners vs. Executives: 15% of practitioners claim full deployment, nearly double the 8% acknowledged by C-suite executives.
This difference in perception highlights a communication gap within organizations regarding the status of Zero Trust implementation. Overall, the landscape for Zero Trust is still evolving, with the majority of entities recognizing its value and actively moving towards it, signifying a significant future growth area in security architecture.
theCUBE Research and ETR @RSA – What We’re Monitoring

theCUBE once again will be broadcasting live from Moscone West at RSA. Our program spans four days of coverage with leading practitioners, analysts, industry CEOs and thought leaders. All the action can be found here on theCUBE’s live broadcast site.
At RSA, we will also engage directly with the cybersecurity community, attending various events, such as a cocktail party SiliconANGLE is hosting alongside the New York Stock Exchange, OpenPolicy and Intel Capital, and collaborating with companies like Elastic. We eagerly anticipate these interactions as an opportunity to further our understanding and assess the pulse of the industry.
As we look ahead to RSA 2024, our focus will be on a number of critical developments and dynamics within the cybersecurity domain. Key points of interest include:
- Security Spending Patterns: Understanding how these are evolving and correlating with the data we have shared is paramount.
- AI Funding: Investigating how organizations are financing AI innovations amidst the need to maintain operational stability. With around 42% of organizations redirecting funds from other budgets to fund AI, the implications for business lines and IT are significant.
- Security Tool Sprawl: Delving into the management of this sprawl is crucial, particularly given prevailing narrative around the topic. The validity of the ETR data is something we stand by, thanks to ETRs meticulous vetting processes and close relationships with respondents, which remain anonymous and protected.
- SecOps Analyst Experience: Exploring how AI can potentially streamline the complex roles of security professionals, who are often compared to air traffic controllers in their stress and necessity for precision.
- Vendor Narrative vs. Market Reality: Testing the prevalent consolidation narrative against actual market behaviors to discern the true state of cybersecurity industry trends.
Our presence at Moscone West in Media Row offers a prime location for networking and sharing insights. We invite attendees to join us for these discussions, and we look forward to the productive exchanges that RSA always facilitates, connecting technology providers, end-users, and investors alike. As always, the convergence of perspectives at RSA provides a comprehensive snapshot of the current state and future direction of cybersecurity.
See you there!
Image DALL·E 3