It’s estimated that organizations spend more than $200B annually on security hardware, software and services globally. That’s a big number. But consider that the economic impact of cybercrime ranges from $500B – $2T annually. There’s even an estimate from Cybersecurity Ventures that says the figure is as high as $9.5T. Each year, it seems the more we spend, the more vulnerable we become, which is especially concerning given the exposure to critical infrastructures. Governments around the world have stepped up their involvement with executive orders, privacy regulations and lots of “finger wagging” at the technology industry and its customers. Frankly some of that is justified. The technology industry does much good but has a subpar record at solving this problem. One premise that we’ve put forth at theCUBE Research is that the industry must find ways to better collaborate and share resources to combat cyber threats. Two firms, IBM and Palo Alto Networks, have joined forces to combine deep expertise, AI and platform approach to better protect organizations from attackers.
In this Breaking Analysis we look at the security landscape and unpack the multi-dimensional relationship between IBM and Palo Alto Networks to better understand how industry collaboration can improve cyber defenses and modernize security operations. With us are two senior executives from each firm, Mohamad Ali, SVP and Head of IBM Consulting and BJ Jenkins, the President of Palo Alto Networks.
Two Stocks at an All-Time High
Just to set the context, both stocks of these firms are performing exceedingly well, both at or near their all-time highs.
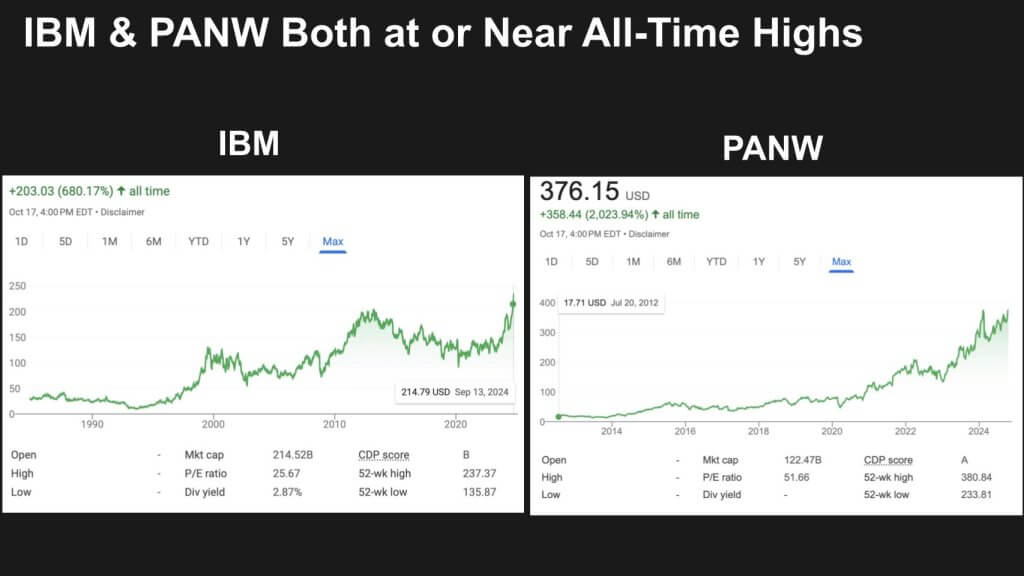
IBM, under Arvind Krishna’s leadership, has improved its focus and is executing on a hybrid cloud strategy with a much more cogent AI strategy, deep consulting expertise, some sharp M&A and a more open ecosystem mindset. The company’s valuation is back up over $200B. Meanwhile, Palo is the first pure play security company to crack the $100B valuation mark attacking the market with a so-called “platformization” approach.
An Expanded and Evolving Partnership
In December of 2023, these two firms announced details of a new partnership with a much deeper relationship.
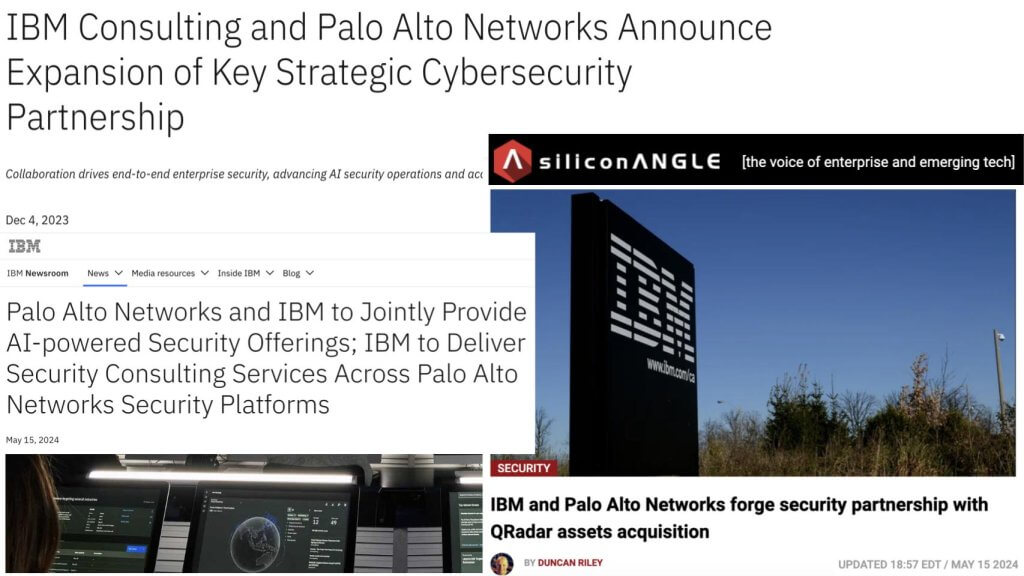
In May of this year, they further advanced the partnership with a sharpened focus on AI security and announced that Palo Alto would acquire IBM’s QRadar SaaS assets for around $500M.
Q1. Mohamad, let’s start with you. We just came off the IBM Analyst Relations Forum in NYC this week. And we heard how you are transforming IBM Consulting, enabling your consultants with AI tools; and embedding more software into your business. Two part question: 1) What was motivation for the partnership with Palo that you announced in May; and 2) Some might look at the QRadar sale and say “wait a minute if Mohamad wants more software in his business why is IBM selling a software asset?”
[Mohamad Ali] Thanks, Dave, and thanks for having us on. It was great to see you over the last couple of days at the IBM Analyst event. Let me just say there’s very sound business logic behind all of this, and I’ll get to that. But these kinds of relationships actually start with people, and there’s a friendship that was the genesis of this.
BJ and I have known each other for a long time. In fact, we used to be competitors. We were both CEOs of businesses that essentially did the same thing—providing cybersecurity and data protection to small and medium-sized businesses. We’ve known each other for a long time. At one point, we even looked at merging our companies, but then we were both acquired by other entities. That’s how we know each other, and that was the foundation for us working together.
Putting that aside, what’s the logic for this partnership? If you think about cybersecurity—and BJ and I both come from a cybersecurity background—it’s about products, services, and data. Data is really the critical element you were talking about earlier; it’s fragmented everywhere. The more data and signals you can see, the better cyber protection you can provide. IBM sees a lot of data and signals, and Palo Alto sees a lot of data and signals. As we bring those together, we can create better solutions for the market.
We can also bring our products together. IBM continues to have a large set of products that provide security and observability. Palo Alto, of course, has an ever-growing set of products. Together, we’re actually building new capabilities on top of that. We’re developing digital workers that utilize these signals, and we wrap it with a service that we deliver to the client. So, coming together was really all about delivering better security—security that nobody can provide today and that only together we can bring to the market.
[Watch Mohamad Ali explain the partnership from IBM’s perspective].
Q1A. BJ, from Palo’s perspective, what was your motivation behind this deal?
[BJ Jenkins] First of all, having a long-term relationship is the best way to build a successful partnership. It helps both Mohamad and me navigate through anything that comes up. When we look at our customers and what they’re trying to do to protect themselves, there’s a challenge: it’s a very fragmented industry. Point solutions have been the answer for many years, but it just hasn’t worked. We see more breaches in the news and more customers suffering. As customers digitize their businesses and undergo transformation, there are more ways for cybercriminals to harm them.
We believe that the ability to platformize—or help customers consolidate their solutions, reduce their operating costs, and build a better security defense—is the way to go. It’s a better approach for customers. However, helping them transform is always the hard part. We feel we build best-of-breed products and platforms, but you need a trusted partner who talks to CIOs, CISOs, and CEOs and can help them understand how to navigate that transformation. This is where the synergy of Palo Alto and IBM comes together.
When we look at the vast array of resources that Mohamad has and how he’s been leading them by leveraging AI and bringing that technology to the forefront, and then marry it with our platforms, we can offer customers a comprehensive approach to modernize their security posture, consolidate and save money on their operations, get more leverage out of their investment, and ultimately achieve better security outcomes.
Finally, this collaboration came together in the SOC and around QRadar. We are investing over a billion dollars in R&D. Our XSIAM platform, we believe, is leading the industry and driving true transformation for SOC and SIEM. I think IBM and Palo Alto Networks recognized that opportunity, and the way to help customers transform most rapidly was for us to do it together. So we’re super excited; we’re really firing out of the gate, and I think this is going to lead the industry down a different path.
[BJ Jenkins explains the relationship from Palo’s perspective].
Q1B. And is it correct that Palo Alto is acquiring the SaaS assets of QRadar, but Mohamed, IBM’s maintaining the on-prem component of that business. And BJ pick up the SaaS asset and your strategy is to identify opportunities to modernize those installations and “platformize.” W’ere going to use that term a lot today; but is this all correct?
[Mohamad Ali] So look, our joint customers are going to need a set of technologies and BJ and Palo Alto, they have one of the best cloud SIEM products. And it makes sense for us to put together our cloud capabilities around SIEM. We have a very strong on-prem version of that. There are clients who are going to need both, and we’ll be able to provide that. There are clients who are going to want to modernize to the leading cloud version of that, and we’re going to help them do that. And then there’s a whole set of other products that we bring together that Palo Alto has in their portfolio that are critical to security, everything from endpoint to firewall and IBM also brings to the table like observability in the Instana and so forth. That whole family of capabilities are necessary in order to provide extraordinarily good security. And so this is one piece, QRadar is one piece of this bigger solution.
[Mohamad Ali explains the hybrid approach the partnership is brings].
Q2. A lot of CISOs tell us that they’d love to get rid of their SIEM, but they can’t because of compliance reasons. And we often asks “Can you turn that SIEM into a more valuable asset instead of an anchor around your neck? ” And so our premise today is the industry needs more collaboration like this to create better security outcomes. So the question is do you have enough data and have you had enough time that you can say you’re positively affecting outcomes through modernization or consolidation? What have you learned so far?
[BJ Jenkins] Well, I’ll jump in first, Mohamad, but I’m sure customers would like to get rid of their SIEM too—but you can’t. If you look at where the world is heading, especially for large public companies, there’s regulation coming that will require you to disclose events within certain timeframes. Attackers now operate much faster than before; they used to linger and take days, weeks, or months to exfiltrate data, but now they do that in hours. Looking forward, that’s going to become minutes.
So your SIEM really needs to drive a security outcome for you. You need to be able to detect attacks not in days or hours, but in minutes. Your ability to identify, isolate, and start remediating needs to be within a similar timeframe—not only for regulatory reasons but also to protect your business and assets.
This is where there wasn’t enough innovation in the space to meet the moment and where technology was going. We saw this coming, invested heavily, and feel we’ve delivered the product to meet that critical time for customers now and in the future. Again, when you pair that with where IBM has invested—leading investments like Watson over a decade or more—bringing those two things together for a customer is really a moment of transformation for them. It’s the moment when they will be able to meet and exceed regulatory frameworks, be very proactive in what they do, and protect their business. We haven’t been able to do that in security before, but I think now is the time we’re going to be able to help customers do that.
A Full Life Cycle Approach
Q3. It looks like you guys are doing a little “dog-fooding” – that’s what we call it. IBM calls it “Client Zero,” Palo Alto probably calls it “drinking their own champagne.” Of course we’re referring to the practice of internal security and IT teams using the product before going to market. So here you have IBM platformizing its internal security with Palo Alto Networks solutions, and Palo Alto incorporating watsonx into Cortex. That makes these deals more real when you use each other’s products; and it shows skin in the game. Mohamad, speak to the idea of driving AI through the life cycle. We’re showing a graphic here that involves digital workers, threat intelligence detection, you’re doing some scoring, you’re brining observability assets and other resources to the table. Please explain your philosophy with this life cycle approach.
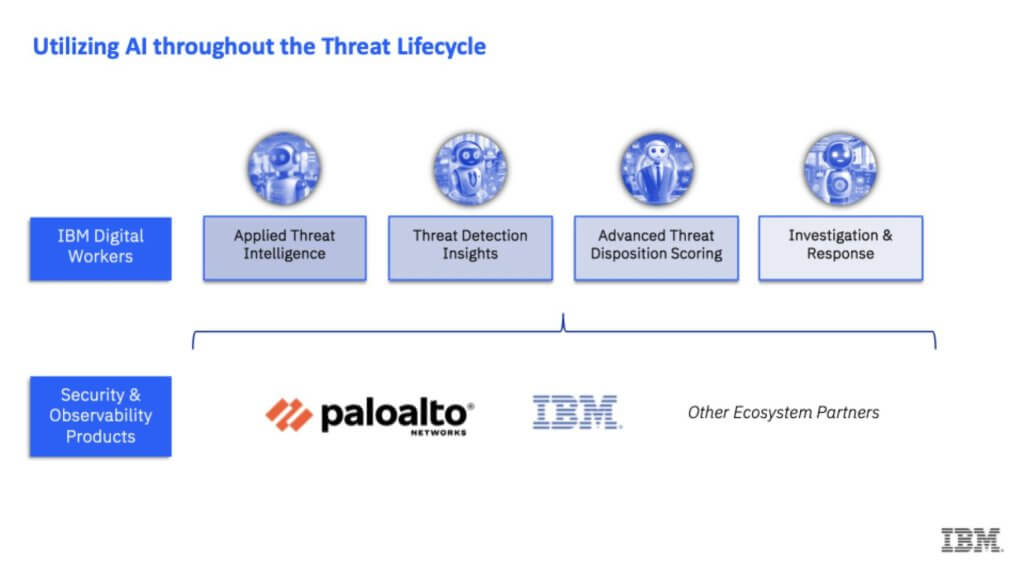
[Mohamad Ali] Yes, yes. BJ touched on it when he mentioned watsonx. watsonx is an AI platform—a great AI platform—but what we do with it is what matters. No AI platform works without data. This collaboration between us and Palo Alto gives us access to a tremendous amount of data—signals coming from the Palo Alto platform and elsewhere. We’re able to use those signals to build a set of digital workers that you just saw earlier. We can deploy these digital workers in the SOC alongside human SOC engineers, who then rely on the SIEM that BJ was just talking about to aggregate all this data and compare it to patterns we’ve seen elsewhere.
We instantiate that through these digital workers. I’m not going to go through the entire lifecycle of a threat, but as people know, lots of signals come in and have to be triaged. Some of them are automatically eliminated; others require someone to look at them. They examine it and say, ‘Hey, this really needs to be investigated.’ To give you a sense, with these digital workers now, we’re able to reduce investigation time by 81%. That’s really essential because more and more signals are coming in as the bad guys are doing more every day. We have to be faster and faster. So what we’re doing is combining these great products and technologies from Palo Alto and IBM with AI to be able to respond faster—because we have to.
[Listen and watch Mohamad Ali explain the watsonx integration].
Q3A. That 81% reduction, Mohamed, is because you’re reducing false positives and you’re identifying through scoring higher priority activities? What’s driving that reduction?
[Mohamad Ali] Yes, we’re using AI throughout the threat lifecycle. The 81% reduction I mentioned occurs near the very end, during the investigation phase, where someone has to analyze a vast amount of data and logs to figure out what’s really happening. This process is very time-consuming. If you think about it, all the data and logs they’re examining are perfect for generative AI (GenAI). You can use GenAI digital workers to extract insights very quickly. So if it used to take someone 10 minutes to review something, now they can do it in two minutes or less because these digital workers are assisting them. It’s actually the perfect use case for GenAI.
[Mohamad explains how they achieve an 81% reduction in investigation time].
The Case for Platformization
Let’s set up the platform discussion. Here’s some data from ETR, our data partner. It’s a survey of nearly 1,800 IT decision makers from this month. We cut the data on the Information Security sector and this XY graphic shows Net Score on the vertical axis, which is a measure of spending velocity and market penetration or Overlap in those 1,775 accounts. Remember this is account penetration, not dollar amounts ok? That’s why Microsoft is off the charts because over 1,000 accounts in this survey are using some sort of Microsoft security tool.
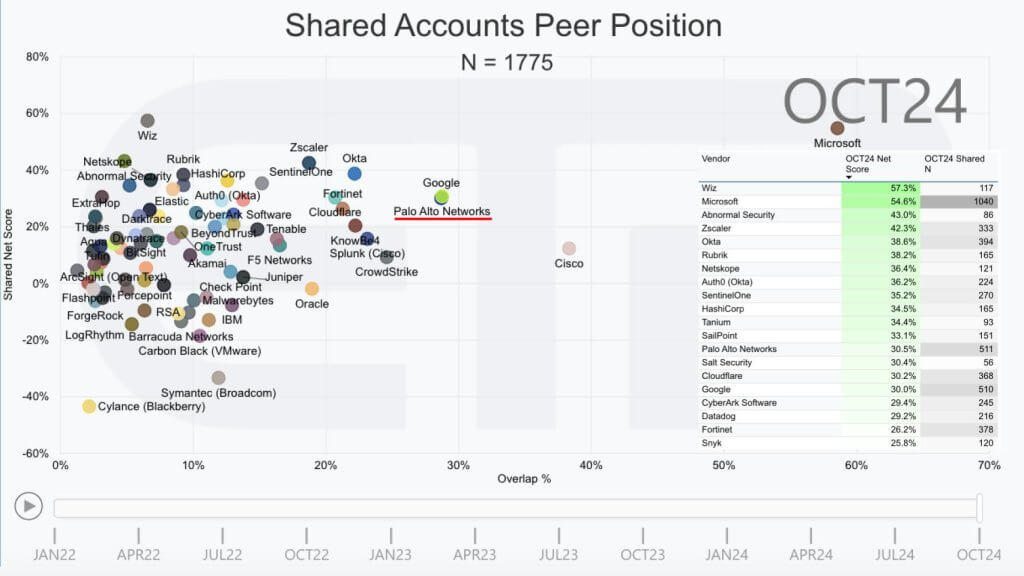
And the point of this chart is: 1) This is a really crowded space; 2) It has some shiny new toys on the vertical axis – Like Wiz, Zscalar is not new but they’re elevated, Rubrik is now a security company – with a $7B market cap. And we’ve highlighted with the red line Palo Alto Networks which is elevated on the vertical axis and prominent on the X axis which is again, market penetration. So the market is really challenging in that, with the exception of possibly Microsoft, no company has more than single digit revenue market share. And we’re talking about a very large market opportunity here with lots of players, lots of tools and a great deal of complexity.
So BJ, Palo Alto uses the term Platformization – Nikesh, your CEO loves to use that term.
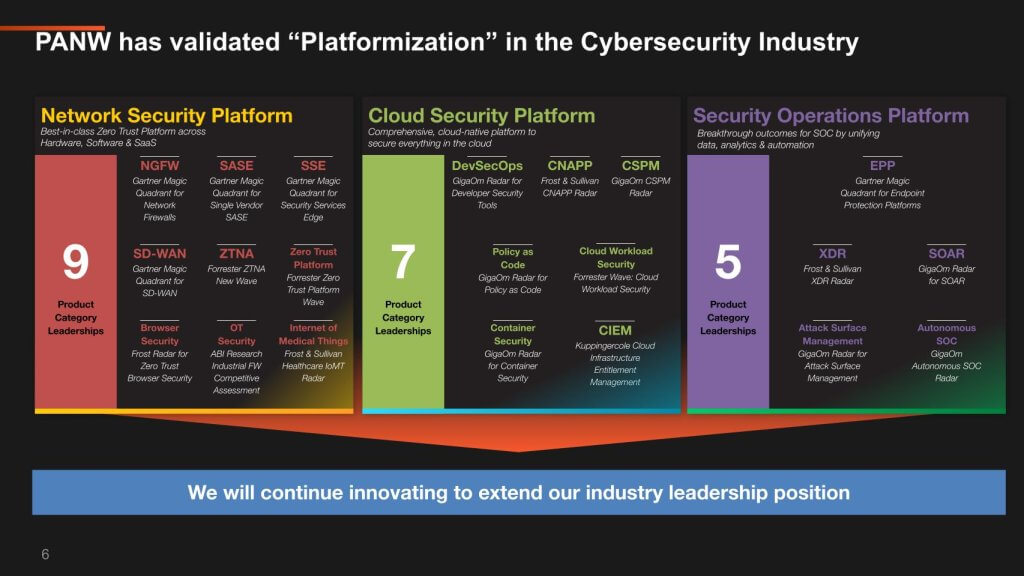
Above is a graphic from Palo Alto Networks that helps visualize the concept of platformization and the point is, you have a lot of products in various sectors and they are best of breed. And this can help customers consolidate and simplify.
Q4. BJ, please address a couple of things. First, What do you mean by Platformization? And second – Can you be both a platform or a suite AND best of breed – that’s very challenging to pull off in such a dynamic industry.
[BJ Jenkins] Yeah, both charts obviously provide insight. I think another point we discuss, Dave, is that the industry has over 3,000 funded companies. The industry has been dependent upon point solutions. Customers have bought point solutions to solve specific problems, and we’ve forced upon the customer the task of trying to integrate those solutions and drive an outcome. As I said previously, it’s not working. We see breaches—we see more and more of them—and we see bigger customer impacts from those breaches. It just tells you that approach isn’t working.
Now, there have been companies in the past that have tried to build platforms, and I think the problem there is they lost focus on innovation. They lost focus on bringing customer value to that platform. How does it help the customer as you consolidate or bring those things together? I think the difference we’re starting to show in our approach is illustrated by the slide you put up, where we have the good fortune of investing over a billion dollars in R&D. I believe we have some of the greatest security minds and product builders in the industry—Nikesh, Lee Klarich, and Nir Zuk—who drive our teams every day to build the best security products for our customers. So we’re not asking customers to forgo quality or innovation to be on the platform. And you have to have that to be successful.
I think the second part of that is our approach has been to focus on three areas: network security, which includes SASE; cloud, or CNAAP; and SOC transformation. In each of these areas, our teams are focused on not only building the most robust platform but also the best individual solutions. What that brings to the customer—and enables consolidation—is a single user interface across each of those platforms. Leveraging the use of data, as Mohamad talked about, we have more data than anybody out there. Ultimately, by doing that, instead of having to buy 10, 15, or 30 point solutions, by purchasing one platform from Palo Alto, you get best-of-breed while saving on operating costs.
You’re able to improve your business processes and, at the end of the day, operate more efficiently, help your business transform, and execute on its goals while achieving a better security posture. And it’s only possible if you make that R&D investment. It’s only possible if you stay ahead of the innovation curve. And if you do that—we see it every day—we reported in Q4 that we have over a thousand customers who have embraced platformization with Palo Alto, and we can see the benefits they gain as they progress on that journey. So I think this is a trend you’re going to see more and more customers adopt. You’ll hear more customers talk about the benefits they get from driving platformization in their environments, and you’ll see the savings, but you’ll also see better security outcomes for them.
[BJ Jenkins explains platformization, what it is and what value it brings].
Q4A. Just to push on that BJ and follow up a little bit because you worked a company, EMC, that made many acquisitions and didn’t do a great job, frankly of integrating. Even IBM has had a mixed track record of successfully integrating its acquisitoijs. Oracle is the exception that proves how difficult it as as it took the company more than ten years to integrate its acquired application portfolio with Fusion. It’s a very expensive and difficult thing to do. Now, maybe it’s easier today in the API economy, but what does it take to do that integration and why are you confident that Palo can succeed in this regard?
[BJ Jenkins] Well, look, I think first off, as compared to my EMC days, we have a much tighter focus. Everything is around security. I think when you look at the infrastructure category that EMC ultimately was trying to play, it was much broader and required a much different set of requirements to try and platformize something. I think in security, we have three very highly focused areas. It’s just about security for us, and I think that makes it achievable. Second is you have to have the ability to invest dollars, which we do. And what I think Nikesh, Lee, and Nir have done brilliantly is they’ve married organic with inorganic.
We tend to look at emerging categories or very tight adjacencies and we make decisions whether to build or buy. If we’re going to buy, we know upfront we’re going to integrate that technology into the platform. And Talon and Dig, which are two of our more recent acquisitions are perfect examples of this. We bought Talon in December and they didn’t release as part of our product until the August timeframe, integrated into Prisma Access. And the way we did that is we added engineers to their team. We built a roadmap that it would be integrated. And I think you have to make that commitment upfront rather than, you see, sometimes they get bolted on or you let them operate independently. And I think that’s just been a fundamental way of how Nikesh and Lee have built the portfolio and we can see customers understand that and appreciate that approach to building a platform.
[BJ Jenkins explains Palo’s integration strategy].
Q4B. Mohamad, what role does IBM play in this platformization initiative?
[Mohamad Ali] Yes, I think IBM plays a pretty big role, and this is another key reason for the partnership—not just bringing the best products and capabilities to the market, but also being able to execute on this platformization strategy.
A couple of weeks ago, I was with the head of IT and security at a very large bank. He said to me, ‘Hey, Mohamad, I think I’m actually paying more than I need to for all these products that I have.’ He probably has at least 50 security products. He continued, ‘I think my risk is increasing, and I’m not able to evolve fast enough.’
So we put a proposal on the table—we had already developed it with BJ and his team—that showed him how, by moving from these 50-plus products to more of a platform strategy, he could actually save money.
But that was only one part of his concern because he knows that over the next few years, threat actors are going to be attacking him a thousand times more, using generative AI to target him. If he’s got all these disparate tools, there’s going to be a vulnerability somewhere. So what he wants is to have fewer tools—the best tools—so he can manage them better. On top of that, he wants to have these digital workers and other solutions we talked about earlier to help utilize those tools to fight back.
It’s really hard to do that when you have 50 products, but if you have a platform strategy, we can make it happen. So we laid out a plan to lower his costs and improve his security, and that’s what you can achieve with platformization.
[Mohamad Ali explains the role IBM plays in facilitating platformization].
Vendor and Tool Consolidation Sounds Great but Customers Struggle to Simplify
Let’s share some more data. This is a survey ETR did ahead of RSA this year.
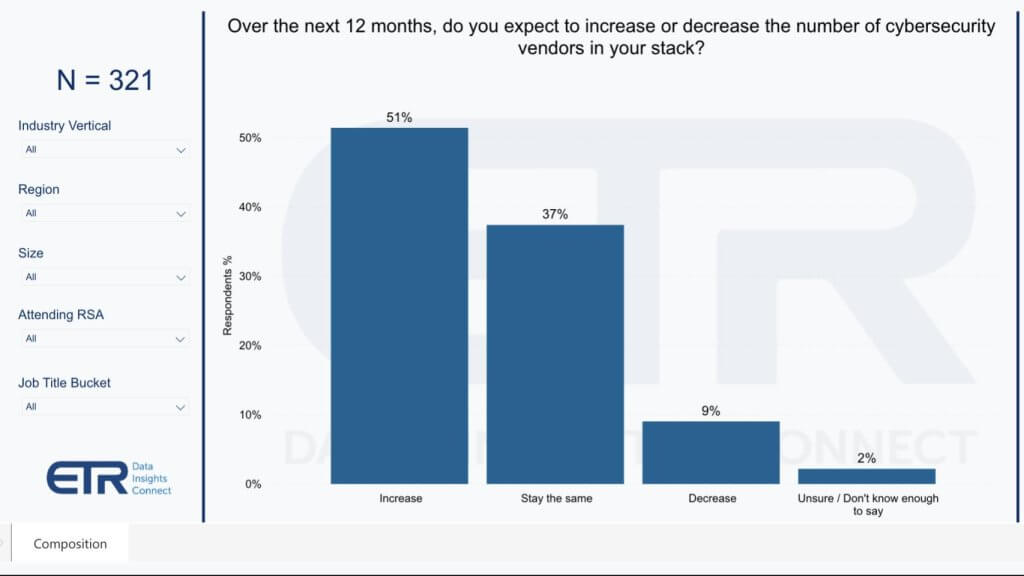
In it we surveyed more than 300 security pros – a nice even mix of C-levels, VPs and practitioners – and the results were consistent across those personae. The question was: Over the next 12 months will you increase or decrease the number of cybersecurity vendors in your stack? Only 9% of respondents say they’ll reduce the number of vendors in their security stack in the next twelve months. While fifty-one percent (51%) indicate the number of tools will increase.
And when we went back and asked why it’s so difficult to consolidate the customers said they’re constantly facing new threats and so they deploy new tools and techniques to stay ahead. Some said – “we need to have best of breed.”
Only 9% of respondents say they’ll reduce the number of vendors in their security stack in the next twelve months. While fifty-one percent (51%) indicate the number of tools will increase.
ETR Survey Ahead of RSA 2024 (N=321)
Q5. BJ square this circle for us. How should we interpret this data? Does it mean big upside for the consolidators like Palo Alto Networks or is there some other dynamic we need to understand that is a blocker to consolidation?
[BJ Jenkins] Well, first of all, the slide tells me I have to do a better job reaching these customers, so we’ll take that as a challenge. There are obviously new technologies coming at these customers that they want to adopt, but sometimes the challenge they face in terms of consolidation is that each of these tools was purchased at different times, so they have different sunk costs. Sometimes it’s about the commercial viability of how you bring those together.
Secondly, there are transition costs. To move off one point solution, you might have to pay twice during that period of transition. You’re probably working with IBM or someone similar who needs to help you in that transition, and there’s a commercial cost there. I think one of the beauties of this partnership, especially in SOC transformation, is that both IBM and Palo Alto have joined together to find ways to eliminate a lot of those, what I would call, ‘double bubble’ or transition costs and consolidate.
We’ve anticipated that. On the Palo Alto side, Nikesh talked about this in platformization—how we approach customers now, and in the effort to help them modernize and take advantage of platforms, we’ll acquire those technologies out there. In contrast to that slide, Dave, we certainly announce our platformizations in our quarterly earnings, and we see a great acceleration in that.
So I think it’s really about helping customers understand the innovation that’s going on, how they can take advantage of that in a platform format, and doing it in a way that meets their budget requirements and drives operational savings. When we can sit down with customers and have that conversation, it really enables them to make that move.
Q5A. Mohamad what’s your perspective on this issue and why it’s so challenging for customers to consolidate tooling? It appears there’s significant upside for your two firms if you can crack this problem but it’s a journey for customers, isn’t it?
[Mohamad Ali] Oh yeah, I think it really is. The deals we make aren’t just about selling you a Palo Alto product or an IBM product. These are five-year transformation deals—some are shorter, like two or three years—but there’s a process we’re going through.
Having said that, the threats are coming faster and faster. I keep coming back to the point that if you just keep buying more products—as 51% of the folks said here—eventually you’re going to run into a problem because some of these products aren’t going to be great. The bad guys are going to get through, and they’re learning faster and faster how to do so.
And AI is not the only threat. In a few years, we’re going to face quantum-safe type problems. So all these products out there that use PKI encryption—if they don’t replace that, it’s going to be a problem. If you’ve bought something and it’s in your environment and hasn’t been updated, then you have a big exposure. There are all kinds of threats on the horizon within the next few years, and I think some of our clients are starting to realize that.
At IBM, we do a lot of work with governments and banks, and they are recognizing that it’s not just the AI threat that’s here—there are more and more looming threats. Having 50, 60, or 70 products is not really the way to go long-term.
Q5B. There’s a fear that once Quantum goes mainstream organizations will be ill-prepared. You know the saying, “exfiltrate now, decrypt later with Quantum.” How are you thinking about that?
[Mohamad Ali] This partnership is so important and so deep. I talked about how we’re doing co-development—joint development around new capabilities that are AI-powered using watsonx and these digital workers, and so forth. But if you think about it, we mentioned quantum just a minute ago. There are now four quantum-safe algorithms out there; IBM scientists developed three of them. So there’s another opportunity for Palo Alto and us to work together to ensure that Palo Alto’s products are quantum-safe going forward, and IBM’s products are quantum-safe going forward.
How many of those 50, 60, or 70 products in independent environments are going to be able to be at the forefront of this? This is why it’s so important for companies like IBM and Palo Alto to come together, because the threat is real and increasing.
[Mohamad Ali explains the quantum threat and opportunity in more detail].
Measuring the Opportunity: Overlap of Palo Alto Products in IBM Accounts
Let’s come back to how these two firms are working together and begin to quantify the opportunity with one more data slide.
Below we show that same two dimensional view. Remember it’s spend momentum on the vertical axis (Net Score) and account penetration on the horizontal axis (Overlap within IBM accounts).
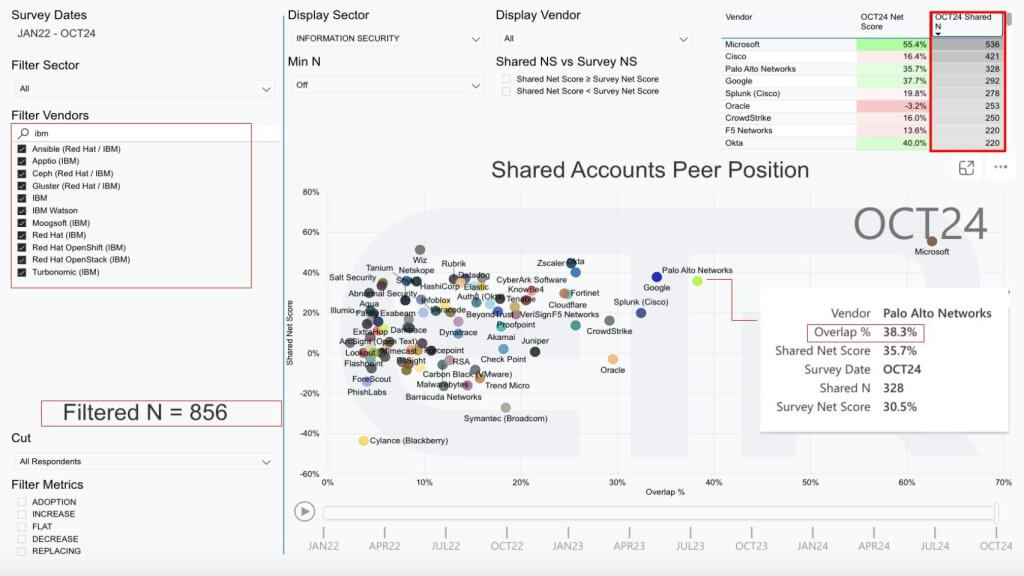
What we’ve done above is filtered the data on 856 IBM accounts in the survey and we’re measuring the overlap in those accounts by each cybersecurity vendor shown. We don’t know what the real world numbers are but in this survey, 328 or 38.3% of those 856 IBM accounts also have Palo Alto Networks security products. That’s pretty significant penetration already with some real upside. Remembker again this is account penetration, not amount spent.
By the way in the F1000, the penetration is around 6 percentage points higher into the mid 40’s.
Q6. Going forward, what should we be looking for in terms of momentum or indicators of success? Will we see higher penetration or is the focus on deeper involvement with these accounts? Should we expect more consolidation? Will we see better security outcomes and what will that look like?
[Mohamad Ali] The 38% is fascinating because that’s a number of companies, but I bet if you did this by revenue, that number would be significantly higher. If you think about it, our clients tend to be the largest on the planet, so I’d say there’s already a pretty high overlap on a revenue basis.
I think a lot of what we’re going to be looking for is penetration. Because, as you showed on [an earlier] chart, companies continue to have 50, 60, or 70 products, and it’s growing. This is an opportunity to bring a more consolidated solution. BJ and I have already seen that. We do these quarterly QBRs where we look at the accounts we’re pursuing, and the penetration is looking quite strong.
[BJ Jenkins] Yeah, I’ve been doing this for a long time, and partnerships always have different arcs. This one, right out of the gate, has been the most incredible I’ve seen, and there are a couple of reasons. First, I just think fundamentally the value proposition we’ve created together is compelling for customers and meets them where they are. Second, culturally, both of our companies are truly customer-centric and want to create customers for life. IBM has been a trusted partner to these companies for decades. As a security provider, that’s what we want to be for these companies. So there’s been a great cultural alignment there.
I think the third part, which Mohamad was just talking about, is that given our presence in some of these large accounts and where IBM is positioned—not only in the SOC transformation with the QRoC [QRadar on Cloud] business but also, as Mohamad said, in the move to cloud or hybrid cloud and zero trust—we have a compelling value proposition together. That’s going to allow deeper penetration, especially when you think of the largest customers in the world.
And we’ve already seen it in just the early days. We’ve not only seen that deeper penetration for both of us, but again, to give IBM a lot of credit, we broke into a major food processor with whom we had never done business before. In this QRoC to XSIAM transition, IBM had the seat at the table—they walked the customer through it, they brought us in, and the customer is now deploying XSIAM. So I believe that chart is hopefully going to show even more penetration in those larger accounts going forward.
[Mohamad and BJ give their perspectives on the opportunity ahead].
Key Issues Going Forward
Let’s share some things that we’re look at in the future here at theCUBE Research. Below are some of the key issues we’re watching. We’ll comment and then each of you can summarize your final thoughts.

At the IBM Analyst Forum this past week, we participated in an Ask Me Anything with Arvind Krishna, summarized on theCUBE Research. He said something quite interesting. When we asked about his philosophy on partnerships, he said, ‘You could look at your competitors that are growing faster than you and say, “Hey, we want a piece of that action.” But today, the mindset is that what we used to consider competitors, we now see as opportunities. Where can we add value, maybe help that competitor grow, and we can grow as well?’ He mentioned, ‘We’ve got seven partnerships now, four of which are over a billion dollars a year, with three others tracking that way.’ So that’s a new mindset for IBM. The example you just gave is a win-win for both companies and the customer.
Now we want to close by highlighting some key issues we’re focused on for the future and then have each of you summarize your final thoughts.
The adversary is highly capable. There are well-funded nation-states like China, Russia, North Korea, and Iran—the big four. You have organized criminals and disreputable insiders. Almost anyone can deploy ransomware today, so risk is on the rise. The probability of an attack is higher than ever, and the impact of breaches is escalating due to ongoing digital transformations. In many organizations, unless you have a strong security posture, your expected loss profile worsens.
Collaboration in tech has been lacking, more is needed. Historically, we’ve seen tech companies somewhat reluctant to share data and collaborate because the industry is so competitive. Are we going to see more industry collaborations like the one between IBM and Palo Alto Networks to effectively combat these threats and help organizations keep pace with agile attackers? Is AI going to make the problem even worse?
Will AI increase threats or help us better defend? Are we becoming more vulnerable because we’re increasingly reliant on technology, or will AI improve the security posture for defenders? Will platformization actually show up in the macro numbers? It doesn’t today; it’s certainly isolated in some of the earnings reports we see. Is this lifecycle approach to security that IBM is promoting going to enable simpler and better security posture, detection, and response? What’s the role of governments and public policy in the battle for better security, defense, and response? Is the private-public sector partnership where it should be? I think it could be better from our perspective. What more can be done in that regard?
Is platformization the answer? Will “platformization” actually show up in the macro numbers or will it be isolated? And will the lifecycle approach to security that IBM is espousing enable simpler and better security detection and response?
Public private partnerships must improve. What is the role of governments and public policy in the battle for better security posture, defense and response? Is the private public partnership where it should be? What more can be done in that regard?
Q7. BJ and Mohamad, thank you for participating in this episode of Breaking Analysis. Please summarize your thought from the discussion and give us your final word.
[BJ Jenkins] Well, each of those questions could be a show in its own right, Dave. But look, I would say that the threat landscape is going to continue to grow, and AI is going to accelerate that. I do think our use of AI can help meet this moment, but I think this partnership will be a trailblazer and a trendsetter in terms of others looking to replicate and get the same benefits. I think it’ll be hard to do, given the base we started with, the IP of both companies, and how we’re coming together, but I suppose you’ll see more of this down the road.
I say that because I believe Nikesh was the first to use the term ‘platformization,’ and I’ve heard five to ten security companies now claim they’re a platform. I believe this one is going to be the most successful. I think it is a trendsetter in terms of how it’s structured. And I would say that Mohamad and I both want to come back because we are going to be that billion-dollar partnership that Arvind mentioned to you the other day. He’s given us the goal; Mohamad and I talk about it all the time. Our aim is to get there as fast as possible.
[Mohamad Ali] Yeah, sure, Dave. The list you just went through confirms that this is a complicated, difficult, and expanding threat landscape for all of us. These partnerships are absolutely essential if we’re going to fight back effectively. That said, the fact that we get to solve these hard problems and get paid for it is actually pretty amazing. And the fact that we get to do it with friends like BJ and Nikesh is wonderful because we’re out there fighting for our clients every day, and you want to do it with friends. So I’ll end where I started: it’s all anchored on these great relationships.