In this episode of the SecurityANGLE, my podcast focused on all things security, I’m joined by Douglas McKee, executive director, threat research at SonicWall for a walk through the SonicWall 2024 Mid-Year Cyber Threat Report. Of one thing we can be certain: the threat landscape is rapidly evolving, and we need to evolve our technology along with it. Reports like SonicWall’s, which take a somewhat different approach and measure attacks equating for time and frequency, help illustrate how metrics can be used to calculate risks more effectively.
Watch: Unpacking the SonicWall 2024 Mid-Year Cyber Threat Report here:
The SonicWall 2024 Mid-Year Cyber Threat Report takes a look at the evolving threat landscape over the first five months of 2024 and I’m not going to sugar coat it: the report paints a rather concerning picture of today’s cybersecurity environment.
One of the most striking revelations for me is the sheer volume and frequency of cyberattacks. SonicWall reported that its sensors detected attack activity for 125% of a standard 40-hour work week, which means there are 50 hours of critical attacks happening in the space of 40 working hours. This translates to organizations enduring an average of 1,104 hours of critical attacks during 880 working hours in the first half of 2024 alone. No wonder CISOs never sleep.
Exploring the Financial Impact of a Cyber Attack
As if the frequency and volume of cyber attacks are not significant enough, let’s look at a cyber attack from a financial standpoint. The SonicWall report revealed at a minimum 12.6% of all revenues are exposed to cyber threats without proper protection. SonicWall’s 2024 Mid-Year Cyber Threat Report highlighted this stat and extrapolated that out to provide an example of financial risk: F=for a $10M company, which equates to a potential risk of $1.2M.
Moreover, this report covers the first five months of 2024, so when mapped out over the course of a full year, a $10M organization, as used in this example, would potentially be looking at an estimated financial risk cost of ~ $30M. It’s important to note that figure is only revenue risk from downtime; there are other impacts, financial and otherwise, of a cyber attack.
Doug explained that with this report, SonicWall has introduced a new metric designed to connect attacks to tangible business impact. He explained this new metric by comparing it to the act of trying to measure rain. Would you count the raindrops, or would you talk about the amount of rainfall over a given period? There’s so much to factor in: different sizes of drops, some bigger, some smaller, and they hit in different places. But at the end of the day, when it comes to rain, we say “Oh, there’s been an inch of rain over the past couple of hours or the last 30 minutes,” etc.
SonicWall approached measuring the impact of a cyber attack by developing a new metric, one developed by looking at the number of attacks happening over a given period of time, in this case, a span of an hour. As we know, time, in general, has a value associated with it. Thus, factoring the impact by using SonicWall’s newly developed metric and by taking the average revenue a company makes in a day and breaking that down into hours, one can attach a finite value to the cost of a cyber attack. If an attack lasted for x number of hours, preventing employees from working during that time, the financial impact of the attack is fairly easily measured.
Malware Continues to be a Primary Tool for Cybercriminals
Not surprisingly, the SonicWall 2024 Mid-Year Cyber Threat Report revealed malware continues to be a favorite of threat actors. The report indicated a 30% spike in malware volume from March to May, and SonicWall further reported a 92% increase in the month of May alone.
In addition, the report revealed that 15% of all malware uses software packaging as its primary MITRE TTP.
I believe it’s a given: malware will continue for the foreseeable future, as it’s a handy part of threat actors’ toolkits. These rising numbers also align with data we are seeing from others in the security ecosystem.
Ransomware Threat Actors Utilize Geographically Tailored Attacks
Much like malware, ransomware continues to be popular, and in many instances, we are seeing ransomware threat actors use geographically tailored attacks. Doug shared that his team at SonicWall has seen a pretty diverse change in numbers across the globe. In North America, for example, they saw a 15% increase in ransomware in the first half of 2024 and a 51% increase in Latin America during that same time period.
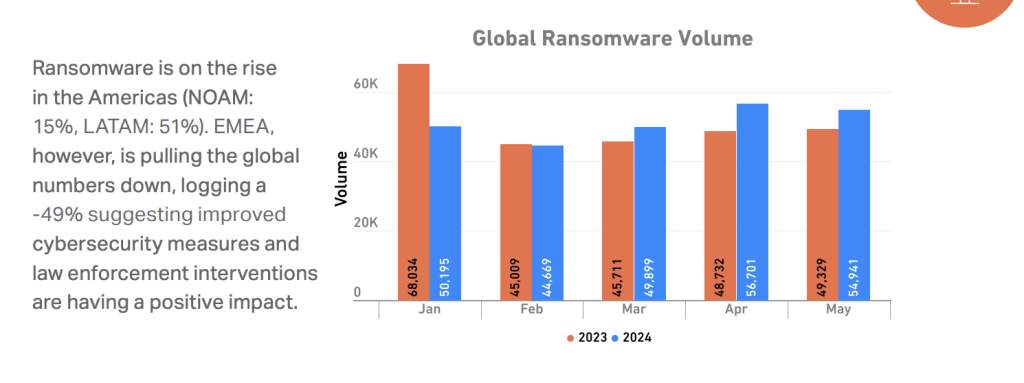
Image credit: SonicWall
He also noted that in EMEA those numbers are much lower, indicating that security teams and the measures they are taking — in some instances aided by law enforcement — are working.
But threat actors typically go where they can do the most damage and potentially reap the most financial game. That’s why we’re seeing the rise in geographically tailored attacks. Some areas are more mature from a security standpoint than others, and attackers are shifting to take advantage of that, like the activity we’re seeing in in the LATAM market.
The IoT: The Vulnerability of Connected Devices Remains a Very Real Threat
As we’ve discussed here many times before, the IoT is and continues to be an attractive target for cybercriminals. The SonicWall 2024 Mid-Year Cyber Threat report indicated IoT attacks have surged by 107% in the space of just five months in 2024. It’s clear the IoT is a sweet spot for threat actors, especially in manufacturing or in the healthcare sectors, which is where we continue to see attacks on a regular basis. But make no mistake, sensors and endpoints are all around us: in our offices, our homes, in smart cities, and in our kids’ playrooms. Manufacturing and healthcare are not the only sectors at risk; they are just highly attractive to cybercriminals because they represent fairly low-hanging fruit. That means they’re a juicy target and can possibly provide a big bang for the buck for criminals as organizations scramble to get their systems back online — and are often willing to pay handsomely in order to do that.
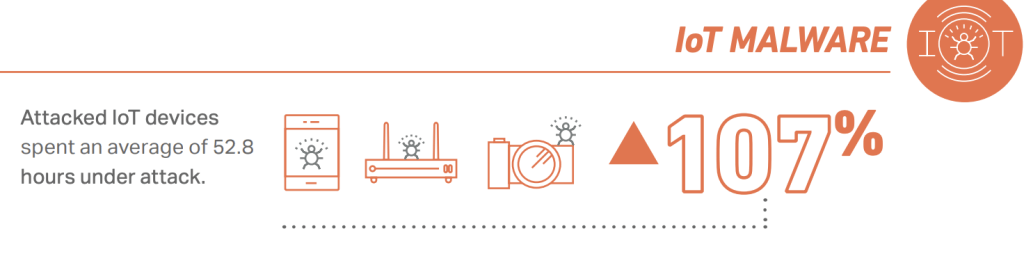
Image credit: SonicWall
Doug highlighted that in the first half of 2024, the top five most widespread attacks in general (not just across IoT, across all attacks) affected the largest majority of customers and partners, and THREE of those attacks targeted IoT devices.
The Rise in Encrypted Threats Signals Threat Actors are Becoming More Savvy
Another area the report highlighted is the rapid rise in encrypted threats, jumping a whopping 92%. This indicates threat actors are becoming more sophisticated (likely aided by AI) and are using encryption to avoid detection. It only makes sense: when unencrypted malware doesn’t work as often, attackers pivot to a different approach. Encryption is well-known to help as a defensive technology, so that’s a key driver for threat actors to switch it up and embrace encrypted threats.
The Rapidly Evolving Cybersecurity Threat Landscape Doesn’t Disappoint
I noted that the report covered “never before seen malware variants”—this refers to SonicWall’s detection engines seeing variants they’ve not previously experienced. Those “never before seen” malware variants occurred in the first five months of 2024 at a total rate of 78,000, representing an average of 526 new strains daily.
AI could well be playing a role here, as threat actors might take an existing piece of malware and use AI to modify it slightly. It’s quick, easy to execute in multiple iterations, and very attractive to cybercriminals.
I’ve said before that being in the cybersecurity business feels a lot like playing a daily game of whack a mole, and a never-ending one at that. Numbers like this reinforce that feeling!
What Now: How Do We Protect Organizations in the Ever-Evolving Cyber Threat Landscape?
One of the things we talk about incessantly here on the SecurityANGLE podcast is the rapidly evolving cybersecurity threat landscape, which is not slowing down any time soon, if ever. As we wrap the show, I asked Doug to share his best advice to organizations, their CISOs, and IT teams, on how to think about this moving forward and how to most effectively combat the ever-evolving cyber threat landscape.
His advice aligns with what other cybersecurity leaders have shared: don’t try to do it alone, that’s where mistakes happen. Hiring more people is rarely the answer, especially given the dearth of skilled cybersecurity talent. Leveraging a partner or a SOC to do 24/7 monitoring is the key to making sure your organization is protected. I’ll also add that I’m a firm believer that visibility is the key to understanding what is happening across your network and ecosystems as a whole and if you don’t have that visibility, you’re flying blind and rolling the dice in a dangerous way. Trying to go it alone, while a noble cause, is likely going to cost the organization considerably more than working with a partner would.
Doug’s other advice is centered on committing to a practice of continuous learning: read or consume ALL the data, not just your own. Reports like this SonicWall threat report, and others of other industry leaders focus on different attack vectors, different verticals and a wide variety of things. Making sure you’re up on what’s specific to your industry will help leaders make more informed decisions. I couldn’t agree more. Data empowers decisions, so if you stay on top of what’s happening across the industry as a whole, and find trusted vendor partners with whom to work, you’re making all the right moves.
All in all, it was a great conversation and the insights coming out of SonicWall’s Threat Report were an informative, helpful glimpse into what’s happening thus far, five months into 2024. Hopefully this conversation and the insights shared provide some guidance you can use within your own organization.
Download the report here: SonicWall 2024 Mid-Year Cyber Threat Report and if you’re heading to Black Hat in a few weeks and are interested in more information, be sure and hit Doug up — I’m sure he’d be happy to talk with you. You can find Doug on LinkedIn here.
See more of my coverage here:
Zscaler’s Executive Insights Mobile App: Serving Up Better Experiences
Trustwise’s Optimize:ai Launches: All Eyes on Gen AI Safety and Security
CISA’s Secure By Design Pledge Continues to Build Momentum: Is it Basic? Maybe, But It’s a Start