In this episode of the SecurityANGLE, Jo Peterson and I break down some key takeaways from Black Hat 2024. We also explored Ivanti’s 2024 State of Cybersecurity Report, along with some of the briefings from the Black Hat 2024 event we were most interested in, and shared thoughts on vendors who either had interesting news and/or cool product launches/updates that we wanted to delve into.
Watch the full episode — Black Hat 2024: Key Takeaways, et al., here
At the beginning of August, some 22,000 IT pros and vendors gathered at the Mandalay Bay in Vegas, enjoying the 105-degree weather and looking for reasons not to go outside. Not only was the weather hot, but the heat has unfortunately been turned up on many security and IT teams in the past month since the CrowdStrike meltdown that occurred in mid-July.
Ivanti’s 2024 State of Cybersecurity Report
Before we discussed key takeaways from Black Hat 2024, including many conversations and lessons learned from the CrowdStrike incident, we wanted to take a quick look at Ivanti’s newly published 2024 State of Cybersecurity Report.
Many firms, including Verizon, Comp TIA, Splunk, Ivanti, and others, regularly produce an annual State of Cybersecurity report, but for the purposes of this conversation, we are going to focus on Ivanti’s 2024 State of Cybersecurity report, which the company designed in a way that spoke volumes to both Jo and me. The Ivanti report features insights from 7,000 leadership-level execs, cyber pros, and office workers, and the findings indicate cybersecurity remains a top priority, even at the board level, for organizations today. We see that as very, very good news, especially increased involvement at the board level.

One of the key standouts from the report was the need for closer alignment between the CIO and the CISO, and getting arms around data silos is a top concern, which aligns with our research on this front. Data silos negatively impact an organization’s security posture, and awareness here is good to see.
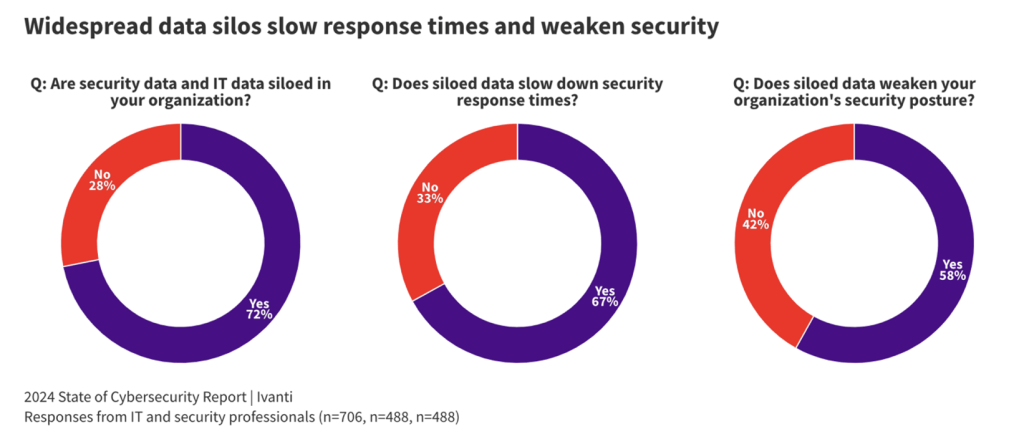
We explored some other nuggets from Ivanti’s 2024 State of Cybersecurity report, which include:
- Budgets are increasing. 73% of leadership-level executives and IT/security professionals report security budgets are on the rise.
- Cyber Budget Investment Areas. 87% say the organization’s 2024 cybersecurity budget is sufficient to meet goals — and they’re investing it across a mix of established and emerging areas — from cloud and data security to identity threat detection and generative AI.
- Gen AI. Nearly half of the survey respondents reported they view gen AI as a net positive for security
- Cybersecurity is key. 91% report cybersecurity is viewed as a core strategic asset within their organization.
- CISOs report preparedness improving. Survey respondents also indicated that security preparedness is improving overall with 57% saying they feel they are more prepared to defend against cybersecurity attacks today compared to one year ago.
They are more prepared, more aware, and have enough budget to do what they need to do — all good news. It’s great to see investments in both established and emerging areas, as well as the fact that boards are increasingly invested in cybersecurity outcomes and are beginning to include members with security expertise. Jo and I both view this as indicative of an important step forward.
Black Hat Briefings Show a Wide Range of Topics and Interests
There are a whopping 24 categories of keynotes and sessions that took place during this year’s Black Hat 2024 event, on topics ranging from AI to Threat Hunting and Incident Response. Taking a closer look at how the 90 or so keynotes/sessions broke out into categories showed where the industry as a whole is focused, which we thought was interesting. These sessions broke out as follows:
- 15% keynotes/sessions were AI-focused
- 15% keynotes/sessions were Offensive Application Security-focused
- ~10% keynotes/sessions were Cloud Security-focused
- 12% keynotes/sessions fell under the category of Enterprise Security
Given that it’s an election year in the U.S., it was also not surprising that two of the keynotes focused on elections and the Presidency: Fight for Secure Elections around the World and A View into Problem Solving from the White House.
Since AI is such a key piece of the conversation at pretty much every industry event, at Black Hat 2024, it was interesting to observe just how security professionals are seeing it fit into their operations as a whole. In IT and Security, we’re all sort of infatuated with new disruptive technologies, and AI has had and is still having its 15 minutes of fame. While there is still very much that shiny new toy feeling around AI, we are seeing a definitive shift away from the hype and a move toward understanding the incorporation of AI and LLMs into existing tool sets and the value that they can deliver. We are now seeing AI becoming more about practical application as it relates to improving threat detection, automating responses, and enhancing overall security posture. At Black Hat 2024, the conversation was centered around integration and delivering real-time benefits, which is exciting to see.
AI briefings during Black Hat 2024 tended to be prescriptive in nature ranging from topics like A Year in the Trenches to Smarter, Faster Security in the Age of AI, showing a move beyond the hype cycle and digging into foundational, practical ways that AI can be a game-changer for security pros and security operations.
Shadow Resources and Hyperscalers
Digging into Cloud Security, another prominent topic, one of the keynote sessions that intrigued Jo was titled: Breaching AWS Accounts Through Shadow Resources. Three security researchers from Aqua Security discussed a sort of daisy-chaining effect wherein some services utilize others as resources as part of their logic/operation. Interestingly enough, it turns out that improperly done, this could lead to catastrophic results.
This talk presented six critical vulnerabilities that the researchers found in AWS, along with the stories and methodologies behind those discoveries, that could allow external attackers to breach almost any AWS account. These vulnerabilities were quickly acknowledged and fixed by AWS and this is just one example of this kind of vulnerability. We think it’s fair to say that this situation of shadow resources could easily happen with any of the hyperscalers, since many services within cloud portfolios build upon one another.
The researchers found vulnerabilities ranging from remote code execution, which could potentially lead to full account takeover, to information disclosure, the potential exposition of sensitive data or even a DDoS instance. The team of researchers shared their story of discovery as we as how they worked to discover commonalities among their findings, as well as the method(s) they developed to identify other vulnerabilities. With cloud footprints becoming so complex, the inter-dependence that plays a role here clearly comes with its own challenges.
Supply Chain and Cybersecurity
If you think about the idea of daisy chaining from a strict Electrical Engineering standpoint (apropos when your cohost is an engineer), it’s a wiring scheme in which multiple devices are wired together in sequence or in a ring, similar to a garland of daisy flowers. But when you broaden the definition, you start to think of topics like shadow resources that have dependencies on other resources, sort of like the supply chain, which we’ve covered often in this podcast series.
In fact, one of the keynotes on the topic of supply chain at Black Hat 2024 was from the CEO and Co-Founder of ThreatLocker, Danny Jenkins, who spoke on Understanding and Reducing Supply Chain and Software Vulnerability Risks, and it was fantastic. Danny is doing a webinar on this topic this week that you can access on demand by clicking that link.
Why do we keep talking about supply chain and cybersecurity? It’s often were cyber attacks happen!. Gartner projects that 45% of global organizations will experience a supply chain attack by 2025 — three times higher than in 2021 — making safeguarding software supply chains more important than ever.
Identifying back doors or unintended vulnerabilities that can be exploited in your environment, especially as software ecosystems are more complex than ever before, is as critical as staying on top of the latest hacking intel.
Cybersecurity Vendors to Watch
You can always count on Black Hat for having some new vendors and/or new products to show off, and Black Hat 2024 did not disappoint. Here are some of the vendors who caught our eye this year:
AppOmni: SaaS Security Offerings. AppOmni, a leader in SaaS security, unveiled new technology advancements to enhance identity and threat detection in enterprise SaaS environments. These include identity-centric analysis with patent-pending log sequencing and user behavior analytics (UEBA), as well as a comprehensive security health dashboard. AppOmni’s SaaS Event Maturity Matrix (EMM) now supports Snowflake and Veeva Vault, offering better log gap identification and incident response verification. AppOmni’s new SaaS Security Health Dashboard provides executive insights into SaaS security posture, aiding scalable security program development and reducing SOC alert fatigue
Securonix: AI-reinforced SIEM. Securonix introduced two new capabilities within its Securonix EON suite — Cyber Data Fabric and Noise Canceling SIEM. These updates are designed to enhance the company’s Unified Defense SIEM solution, targeted at helping CyberOps teams tackle sophisticated cyberattacks more effectively. Cyber Data Fabric offers modular architecture for intelligent data classification, ensuring relevant data is analyzed, stored, and archived efficiently. According to Securonix, this integration improves cost efficiency by up to 30%. Noise Canceling SIEM leverages AI to reduce alert fatigue by 50%, focusing on critical threats and minimizing false positives. This capability includes automated SOAR playbooks for faster response and reduced incident impacts.
Qualys: Patch-less remediation. Qualys has announced TruRisk Eliminate, a new remediation solution designed to enhance risk reduction beyond traditional patching methods. Unveiled at Black Hat 2024, TruRisk Eliminate offers patchless approaches, including targeted isolation and advanced mitigation strategies to address vulnerabilities when patching is impractical. The solution is designed to address the challenges of unpatched vulnerabilities, which can lead to significant security risks including ransomware attacks and data breaches. Key features include TruRisk Mitigate for deploying risk mitigation controls and TruRisk Isolate for quarantining risky assets. It integrates seamlessly with IT operations tools like ServiceNow and JIRA and automates complex risk remediation tasks via Qualys Qflow.
Varonis: AI-Powered Data Classification. Varonis Systems has announced new AI capabilities aimed at enhancing its data classification engine by leveraging machine learning to discover, understand, and classify customer data efficiently. Varonis claims these AI classifiers require minimal training and allow local data scanning without needing to transfer data outside the customer’s environment. Additionally, in a bid to ensure transparency and flexibility, Varonis is offering adaptable and easy-to-validate AI models. This expansion is targeted at facilitating effective data classification, improving risk prioritization, exposure remediation, and security control enforcement.
NetRise: Expanded XIoT. NetRise announced an $8M funding round in late April, to advance Extended Internet of Things (XIoT) security technology by way of a cloud-based SaaS platform. At Black Hat 2024, NetRise announced expansions on its NetRise Platform, now supporting the analysis of containers and Windows software assets. This enhancement offers improved visibility across the software supply chain — see how supply chain is becoming a key theme here — enabling security teams to inventory and control software assets and address risks. Key features of NetRise’s XIoT tech include machine learning-based software composition analysis (SCA), enhanced software extraction, and dependency mapping.
Beyond Identity: RealityCheck. One of the vendor solutions I’m very excited about is Beyond Identity’s RealityCheck, an identity assurance plugin for Zoom. We’ve talked here before about the security risks that enterprise collaboration and communication platforms pose, and I think this is a smart solution and one that is well-timed. Beyond Identity’s RealityCheck protects against AI deception, including impersonation attacks and deepfakes, by certifying call participants with Authenticator Assurance Level 3 (AAL3) and device security verification. The feature adds authentication badges, displays risk data, and verifies users and devices. Initially launched for Zoom, Beyond Identity plans to extend RealityCheck to other communication platforms like email and chat.
HPE: AI-Powered Networking Powered by Advanced Security Features. I wrote about this earlier this week, but it bears mentioning that HPE Black Hat 2024 announcements included a significant expansion of its security-first, AI-powered networking portfolio, centered around HPE’s Aruba Networking Central platform. HPE introduced behavioral analytics-based network detection and response capabilities. HPE also announced the enhancement of its cloud-based universal Zero Trust Network Access approach by extending its reach to campus-based local area networks.
Endor Labs: Upgrades Impact Analysis, Endor Magic Patches. Endor Labs, which I will mention was one of four finalists in Black Hat’s 2023 startup competition last year, launched two capabilities to address challenges in the Software Composition Analysis (SCA) market, particularly the difficulties associated with upgrading open-source software (OSS) dependencies to fix vulnerabilities without causing breaking changes. Endor Labs’ newly introduced Upgrade Impact Analysis will enable AppSec teams to assess the difficulty of upgrades, helping them prioritize security fixes and make informed decisions based on potential impacts. Additionally, Endor Magic Patches provide backported security patches, allowing teams to mitigate vulnerabilities when upgrading is too complex or time-consuming. These capabilities are designed to streamline the remediation process, reduce developer workload, and enhance security measures without compromising software stability.
Checkmarx: Container Security Solution. Container security continues to be an area of focus in the cyber space. Checkmarx has launched a Container Security solution as part of its cloud-native Checkmarx One application security platform. This solution aims to boost team efficiency by integrating security seamlessly into familiar development workflows while offering early vulnerability identification, actionable insights, and streamlined mitigation. Leveraging Sysdig runtime insights, Checkmarx Container Security combines static analysis with runtime monitoring to provide a comprehensive view of container security. Cleckmarx claims the solution is unique in its ability to identify and flag malicious packages and that it enhances proactive response capabilities, helping organizations improve their security posture.
Wrapping up Black Hat 2024
To wrap up our overview of Black Hat 2024, it’s fair to say that security is never boring. In fact, nerds like us are excited by the fact that security is finally getting the respect it deserves as a foundational part of business mission-critical operations.
It’s an amazing time to be in cybersecurity: there’s lots of traction in the industry, tons of legacy players doing exciting things, and a raft of exciting companies bringing innovative solutions to the table. What is most exciting, for us anyway, is the fact that cybersecurity has “earned” a central role as it relates to business operations, boards are beginning to understand the importance of cybersecurity as it relates to business resilience and continuity, and boards are evolving to understand the importance of having members with cyber expertise engaged and involved. We are here for it!
Image credit: Pexels, Chris F.
See more of my coverage here:
HPE Fortifies AI-Powered Networking Portfolio with Advanced Security Features
Zscaler ThreatLabz 2024 Ransomware Report Highlights with Brett Stone-Gross
Combatting the Cybersecurity Risk Posed by Enterprise Collaboration Tools



