Zscaler’s Zenith Live 2024 event was held last week in Las Vegas. Highlights included keynotes from Zscaler execs, customer use case examples across a number of industries, partner features and alliance news, and was capped off by a keynote by one of my favorite cybersecurity experts, investigative reporter Brian Krebs, author of Krebs on Security.
Zscaler Zenith Live 2024 Highlights
Zscaler’s value proposition is multi-faceted. It includes:
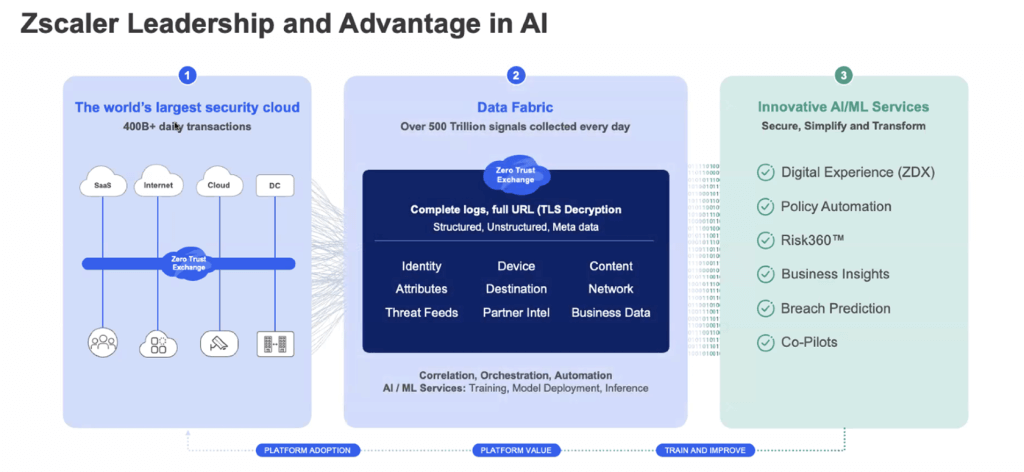
- Zscaler Security Cloud. Zscaler touts itself as the “world’s largest security cloud.” Zscaler Security Cloud scans some 400+ billion daily transactions to ensure the bad things stay out and the good things stay in. These transactions are internet bound from IoT devices, the workforce, as well as workloads.
- Data Fabric. There are the data fabric capabilities made possible by Zscaler’s recent acquisition of Avalor’s Data Fabric for Security, which not only provides customers with the ability to proactively identify and predict vulnerabilities but also helps improve operational efficiencies and performance optimization while also enabling the shift to zero-touch operations moving forward. The goal with Data Fabric for Security is to bring in all the rich telemetry and intelligence that you can see in an inline platform, then contextualize it using third-party signals from the collection of security tools in the enterprise security stack. Not only will this improve detection efficacy policy enforcement, but moving forward, it will allow Zscaler to build different use cases on top of this platform.
- AI/ML Services. Last but certainly not least, there are Zscaler’s AI/ML Services, which include digital experience, policy automation, Risk360, business insight, breach prediction, and copilots.
It’s no stretch to see that the combination of the three: security cloud, data fabric, and AI/ML services combine to make Zscaler a security industry force to be reckoned with.
The overarching goal is to bring in all the rich telemetry and intelligence that can be seen in an inline platform and then contextualize it using third-party signals from all the security tools commonly found in the enterprise security stack. The goal is to further improve detection efficacy and policy enforcement, and also then further innovate by building several different innovative use cases on top of the platform.
Zscaler’s Comprehensive, Integrated Platform
At Zscaler Zenith Live, the company kicked off the event by showcasing a comprehensive and integrated platform designed to bring everything together in one place.
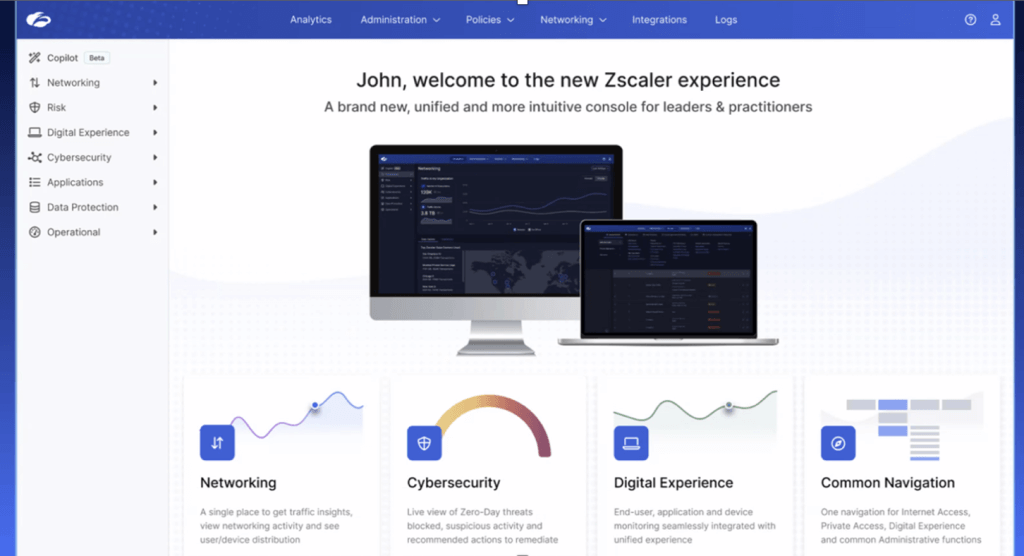
This is designed so that users can quickly see all analytics across cyber, networking, data protection, etc., in a single place and in real-time. Big news coming out of the event included the introduction of a new “Zscaler experience” across all products, along with significant uplift to core services around identity and adaptive access, automation and programmability. and analytics and copilot.
The new Zscaler experience starts with configuring all the products in the Zscaler portfolio and their analytical capabilities in a common portal. I see this as a strategic and well-thought-out move. This brings together specific use cases and the personas customers currently use into one platform, which is important as we see persona consolidations happening across the industry.
Users can quickly see all the analytics across different functional areas (e.g. cybersecurity, networking, digital experience, or data protection) in a single place. For example, in cybersecurity, Zscaler provides a real-time view of all the threats they are blocking. Users can also see interesting zero-days that the Zscaler team is seeing in their environments and what those threats are, where they are coming from, and users can simply click and see the full details of the incident.
For example, in the below example, a user can see a specific sandbox incident when Zscaler identified a zero-day file, and what that zero-day file was seen in the user’s environment. It also shows how many systems it has impacted and can then correlate that to high-profile threats, which could be targeted attacks on a customer’s environment.
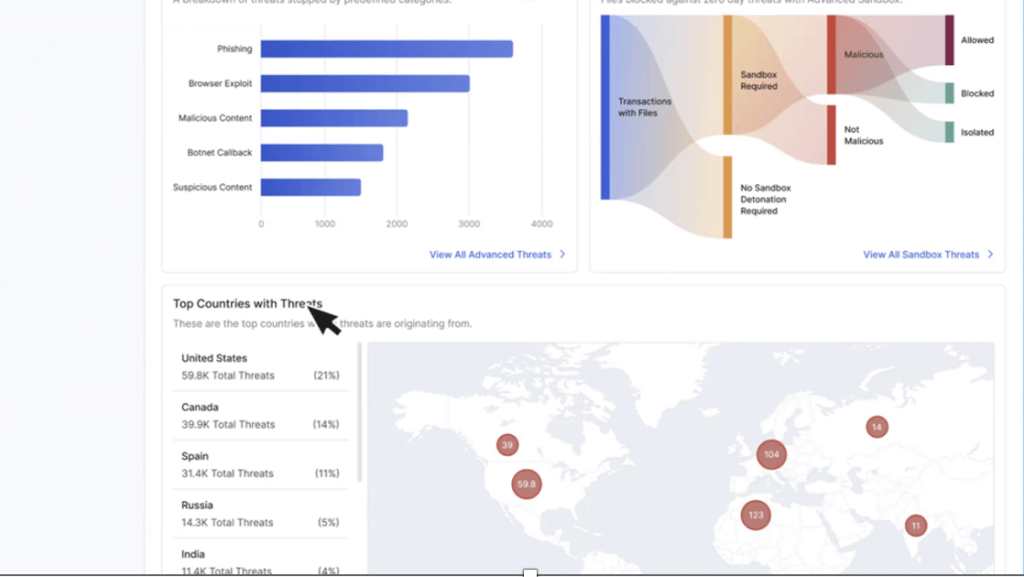
One of the things I thought most beneficial for Zscaler customers on this front is that they can not only see what a threat in the environment is but also quickly see if Zscaler can cover that threat with the current customer licensing agreement. If it’s not enabled in a user’s environment, it can be enabled with a single click.
The beauty for users is clear: all use cases across the entire Zscaler portfolio are available in a single place. Zscaler has also announced the introduction of a common policy for all web products so that you can see internet and SaaS, private applications, clientless applications (cybersecurity, data protection, etc.) and all policies defined in a single place. I see this as being incredibly helpful for customers, with contextual policies for applications, users, and locations that customers want to protect all in one place, in the platform.
A Look at Zscaler’s Newly-Announced Breach Prediction Solution
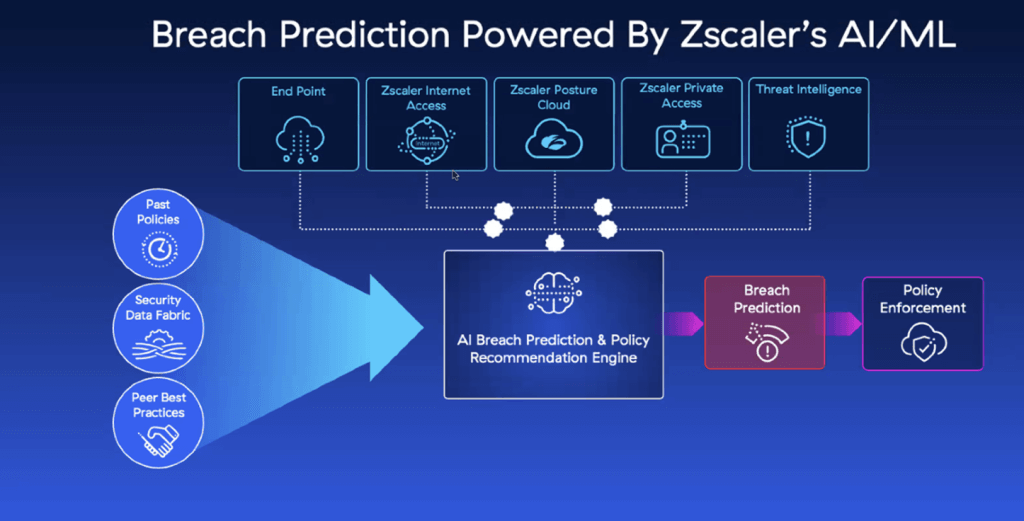
Zscaler’s Breach Predictor is one of the newer innovations announced by Zscaler at Zenith Live. With this solution, Zscaler combines all visibility from the endpoint, internet access, the Zscaler posture cloud where they are doing DSPM and data security-related workflows, and private access (the east-west traffic). Breach Predictor will then contextualize this information with global threat intelligence, bringing in the context from the policies on how customers are configured, what industry peer configurations look like, and then leverage the combination of both gen AI and predictive models to detect potential breach-like scenarios and provide recommendations to help mitigate risk.
During his end-of-day keynote on day two, Chief Product Officer Deepen Desai shared that Zscaler has no intention of stopping here: they want to go one step further. They don’t want to simply identify breach-like scenarios happening as quickly as possible; the goal is to provide speedy notifications to the organization at risk along with recommendations for mitigative policy actions (e.g. blocking access to certain internet-bound destinations, containing an endpoint and not allowing it to communicate with any external applications, or cutting off access to all the assets that an endpoint has access to).
Zscaler’s Breach Predictor is in limited availability today, with about a dozen partner customers. The goal is to go live over the course of the news few months.
The ability to proactively get in front of breach predictions makes every CISO rest easier. Zscaler takes the east-west traffic and contextualizes it with global intelligence, with the ability to look at not only how customers are themselves configured, but also take into consideration the configurations of industry peers. The Zscaler Breach Prediction solution will then leverage gen AI and predictive models to predict breach-like instances. The goal here is to identity potential issues and notify customers as quickly as possible.
The below graphic is an example of what a breach funnel looks like on the Zscaler Breach Predictor dashboard, demonstrating what the product will do. This is what the product screen looks like.
As you can quickly and easily see in this example, there are five users at risk, and lateral movement is a concern, as is the risk of data loss. For these five users, the threat actor has managed to go from the compromise stage to potential lateral propagation and then some indication of data loss. Zscaler will further compute this at all the stages of the attack.
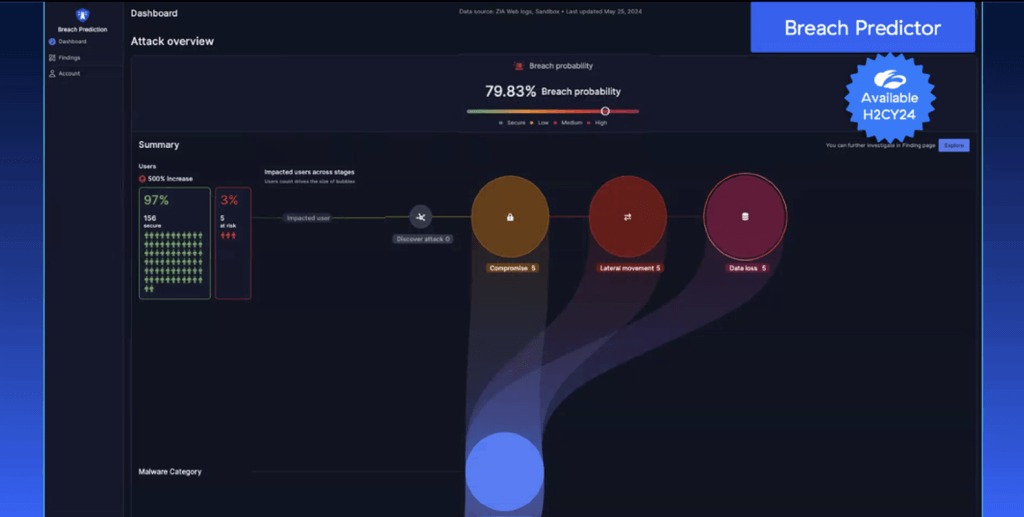
The dashboard will not only indicate a breach probability, it will also call out severity. A user can click in and see the entire attack path an attacker is taking, with the goal being the speedy identification of potential breach scenarios as early as possible in the attack process. As you can see from the above dashboard example, for these five users, the threat actor has managed to go from the compromise stage to the potential lateral propagation, and there is also some indication of data loss. In the above example, you can see the number of users increased to 15, due to whatever additional activity happened within the environment.
The Zscaler Breach Predictor will also showcase the malware or exploit tools that were involved, allowing a further drill down on responding to these attacks or breach-like scenarios.
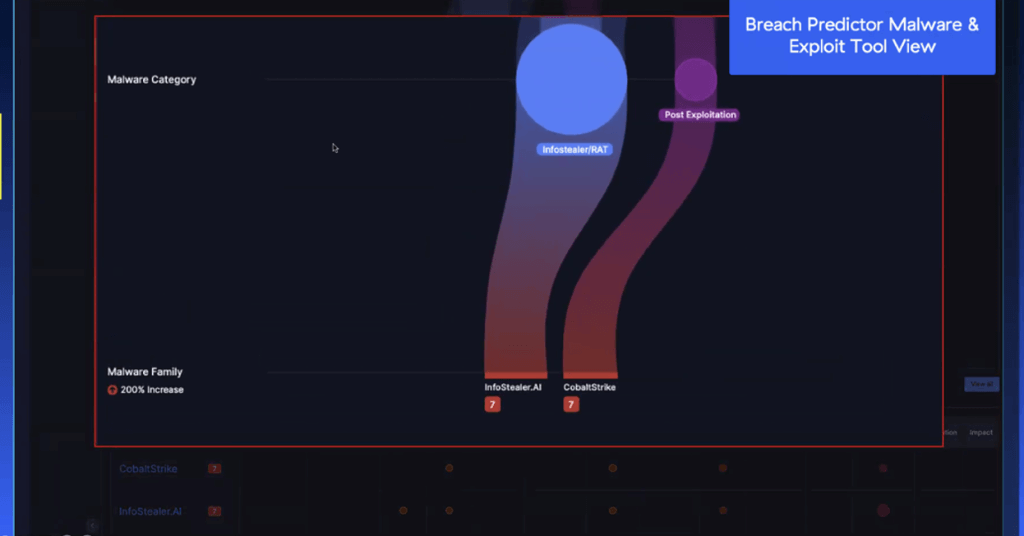
In this instance, referencing the image above, you can see a cobalt strike payload was planted as part of the lateral propagation stage to move within the environment, and then in this scenario, right before the data exploration starts, the Zscaler breach prediction product will call out, “Hey, this is like 100% breach scenario, because we’ve seen all the telltale signs, including about eight severity for info stealer that was observed in your environment, where we’re seeing data exfiltration happening over HTTPS channel.” Users can click through this and see the entire attack path the threat actor is taking in the environment and saving a whole lot of headaches along the way.
There was other news coming out of Zscaler’s Zenith Live 2024 event that I’ll cover separately, but this is a look at some of the platform innovations the team at Zscaler announced that were particularly impressive. Stay tuned!
See more of my cybersecurity coverage here:
Talking Microsoft Copilot for Security with Cyber Expert Rob May (SecurityANGLE podcast)
Trustwise’s Optimize.ai Launches, All Eyes on Gen AI and Efficiency
A Dive Into Software Supply Chain Security with Schneider Electric’s Cassie Crossley
and find and follow me on LinkedIn and Twitter/X if we’re not yet connected.