Oracle’s Strategic Blueprint for Unified, Multicloud, AI and Data
At the Oracle Database+AI Analyst Summit, Oracle outlined its vision for a unified, multicloud, AI-ready data infrastructure. This analyst brief explores how Oracle is integrating AI directly into its database platforms, unifying support for diverse data types like relational, vector, JSON, and graph, while delivering high-performance, cost-effective solutions across multicloud environments. With an emphasis on real-world ROI, AI personalization by user persona, and a pragmatic approach to AI application development (GenDev), Oracle is positioning its database as the foundation for next-generation enterprise AI.
How CloudBolt and StormForge are Making Cloud Cost Optimization Actionable
Only 13% of organizations have mature FinOps programs. Learn how CloudBolt and StormForge help platform teams automate Kubernetes cost control and scale FinOps adoption.
Navigating the Next Chapter of Cloud-Native Innovation with AI, APIs, and App Dev
Explore insights from Traefik Labs CEO Sudeep Goswami on how AI is accelerating application development and reshaping API management, edge deployment, and enterprise governance strategies.
Miratech Brings Strategic Clarity and AI Enablement to Cloud Contact Center Transformations

Enterprise Connect 2025 – Orlando, FL At Enterprise Connect 2025, Miratech showcased its unique approach to helping enterprises navigate cloud migrations, AI adoption, and digital transformation in the contact center space. In a conversation Erik Delorey, Senior Director of Innovation at Miratech, provided insights into how the company serves as a technology-agnostic advisor and implementation […]
272 | Breaking Analysis | Google’s Cloud Play — Integrated AI Across Infrastructure to Apps

We estimate that Google’s Cloud business will exceed $50B in annual revenue this year with Google Cloud Platform comprising more than 50% of its cloud revenue for the first time ever. Why is it then that Google’s cloud business, a $50B+ entity growing deep into the double digits gets so much criticism? The answer is simple. Google’s cloud, with arguably the best technology in the industry, is 2.5 – 3.5 times smaller than the cloud businesses of AWS and Microsoft.
HPE Aruba Networking Central Offers New Deployment Models
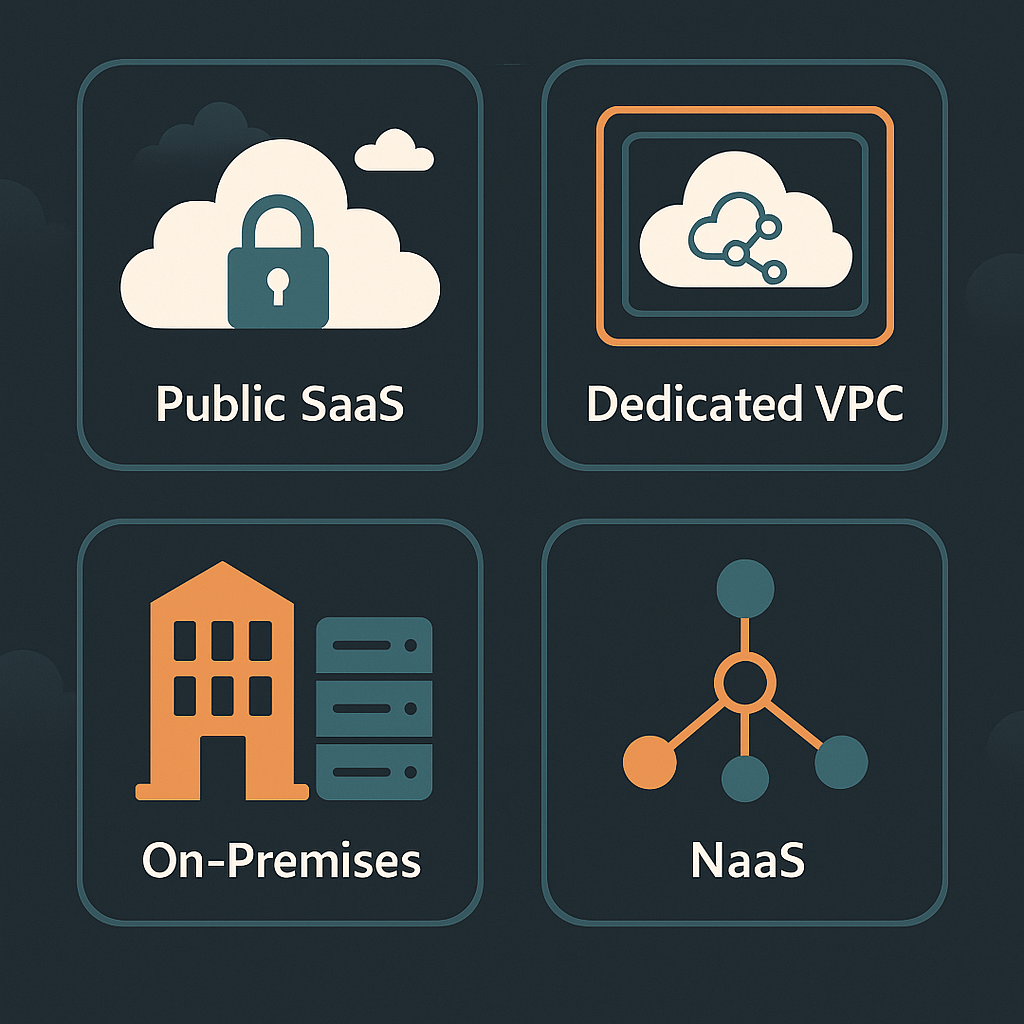
On April 8, 2025, Hewlett Packard Enterprise (HPE) announced an expansion of its network management platform, HPE Aruba Networking Central, introducing new virtual private cloud (VPC) and on-premises deployment options. The move is designed to address enterprise and government requirements for data sovereignty, regulatory compliance, and deployment flexibility. The new offerings build on Aruba Central’s […]
Riverbed Enhances Unified AIOps Platform

In an era defined by digital complexity and AI acceleration, organizations are facing growing pressure to ensure seamless performance across increasingly distributed IT environments. Enter Riverbed: a pioneer in observability and performance monitoring, now raising the bar on its unified AIOps platform vision and capabilities with significant enhancements unveiled this week. Riverbed introduced a series […]
Building Performant, Portable Apps for AI and Beyond
Discover how WebAssembly and serverless design patterns are transforming AI and edge computing. Learn from Fermyon CEO Matt Butcher how developers can build performant, portable apps for real-time workloads.
The New Rules of Application Development in the AI Era
AI tools can accelerate app development, but they’re no substitute for sound engineering. Learn from Google Cloud’s Chief Evangelist how to balance speed, structure, and strategy in modern software delivery.
